In this article, we describe various applications of tokenization in card-not-present transactions – when plastic cards become digital tokens. For example, this could be when a customer buys goods on the internet, or a mobile payment (which encompass mobile wallets and mobile money transfers).
A multi-pronged approach combining EMV, encryption and tokenization is the most effective way for protecting cardholder data. For the purpose of this article, we focus on tokenization, with the understanding that it is only one component of an effective data security strategy.
Tokenization: under the hood
The following describes a clear example of a token implementation in a Card-Not-Present (CNP) scenario.
- The Merchant, is a private company selling products online, for example, T-Shirts.
- The Tokenization Service provider (TSP), is an established firm with long-term experience in security.
- The P2PE provider is a provider of point-to-point encryption service. It could be the same as the TSP.
- The merchant website which interacts with the customer (cardholder).
At first, the Primary Account Number (PAN) is being submitted by the customer to the merchant website.The merchant website transfers the PAN to the TSP via point-to-point encryption, then the TSP stores the PAN in a token vault and sends a token to the merchant website.
The merchant website will then send the token to the credit card processor along with cryptogram information. The credit card processor will request the TSP to de-tokenize the token to retrieve the banking information and change the corresponding account to the cardholder bank. Authorization is forwarded to the merchant which stores it with the token in a database. The transaction is then approved and the customer is notified.
There are many possible implementations and many other data could be tokenized. The token itself… could be tokenized then stored into the database.
The Samsung pay tokenization example
Let’s look in detail at how tokenization works in practice by analysing the case of a mobile payment system: Samsung pay.
Samsung Pay (the NFC payment system developed for the Samsung devices) is a good example of an actual case of tokenization which combines HCE (Host Card Emulation) and “classical” tokenization.
The Samsung tokenized PAN is named a “token PAN” or digitised PAN (DPAN). The DPAN hides the real credit card number and therefore prevents the card number from being leaked.
The Samsung Payment computes a unique cryptogram from the payment information and the DPAN in order to provide a way to show the payment network that this token is valid.
Samsung Pay primarily utilises the tokenization services offered by global payment networks depending on the card issuer. However, third party tokenization services are also supported.
In fact the DPAN is not linked to the PAN but to the FPAN, the Funding Primary Account Number and the DPAN acts as a virtual credit card number as well as a token. So, even if the card has to be renewed, there is no need to change the DPAN. But that ‘virtual credit card’ is resistant to leaks and even having the knowledge of the value of the DPAN, a fraudster couldn’t do much.
The following example presents a typical workflow in Samsung Pay:
- Initially, the cardholder enrols his card to a TSP (Token Service Provider) that is designated by the card issuer.
- A token, the DPAN is generated in the card vault of the TSP and securely sent to the Samsung device where it will be stored.
- When the cardholder performs a transaction, the token, the payment information, and the cryptogram are sent to the payment network through the acquirer. The token is unmapped and the real PAN, in fact, the FPAN is sent back to the payment network, which will ask the issuer bank to charge the account.
- During the workflow, the cryptogram is authenticated as a proof of the validity and authenticity of the transaction request.
- The authorization is eventually sent back to the merchant.
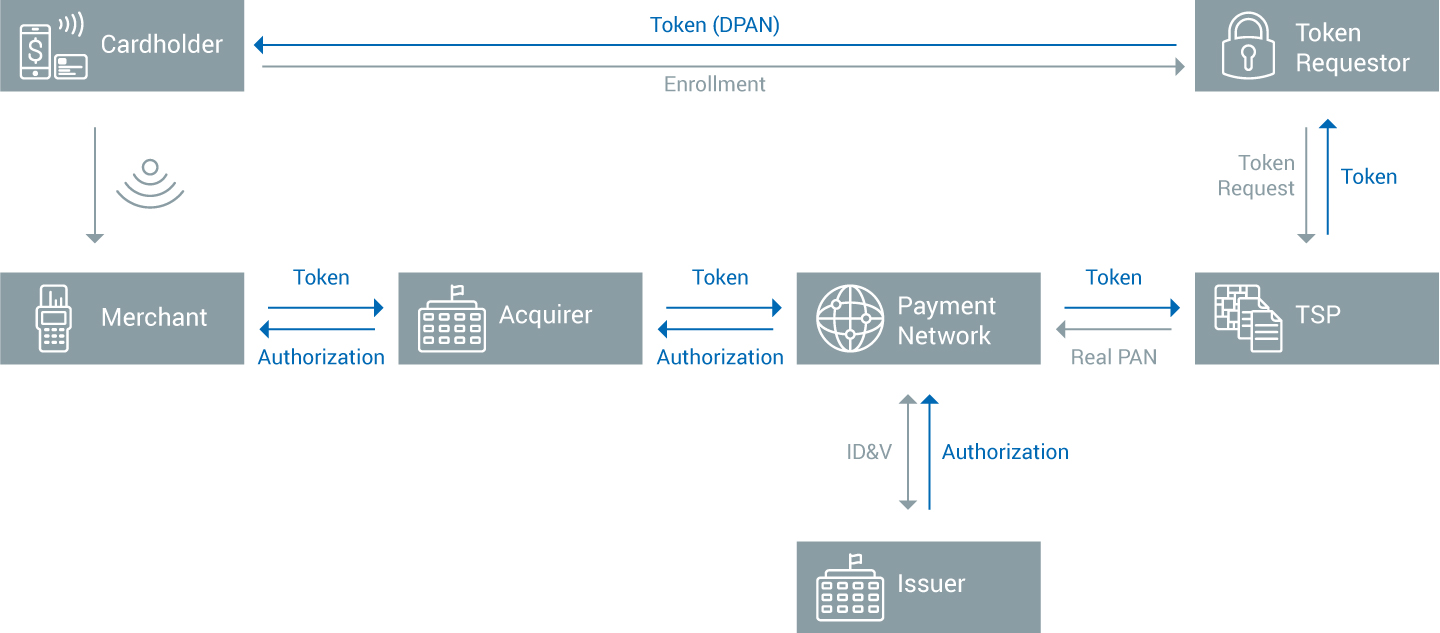
As one can see, well-thought out credit card tokenization is an essential part of Samsung Pay security. Even if the phone, quite secure in itself, would be hacked, only useless information would be leaked.
Tokenization and mobile provisioning: TSPs
Tokenization is very important in the world of mobile payment because the provisioning of keys, personalization of the secure elements and other initializations is done over the air (OTA) and therefore tokenization provides a good security to resist any possible tampering.
With the development of OTA personalization of mobile payments devices, Token service providers appeared. Here is a list of token providers.
TSPs are now a vital component of a personalization chain and an important component of the payment networks. TSPs often also work with Host Card Emulation (HCE) technology which completely de-materialize a payment card, offering only a ciphered tokenized software image to the payment terminals while the “real” card is securely hosted remotely.
The EMV consortium works actively on such topics and a virtual tokenized chip-based payment card may, in the future, become the next standard. After all, the EMV standard requires that a significant amount of information can be retrieved from the chip card without any authentication and tokenization may be applied to all of this data.
Tokenization has definite benefits for both customers and the payment industry, and is a key component of future payment systems, bringing security and trust across the payment ecosystem - the risk of data theft is virtually eliminated because of tokenization.
Related Solutions
The Utimaco KeyBRIDGE TokenBRIDGE offers a complete tokenization solution to prevent organizations from data loss and guarantees unique tokenization of assets without complicating security management.
TokenBRIDGE implements a secure, easy-to-manage Token Vault - the core of any tokenization solution.
Blog post by Martin Rupp, a cryptographer, mathematician and cyber-scientist. He has been developing and implementing cybersecurity solutions for banks and security relevant organizations for 20 years. Martin currently researches the application of Machine Learning and Blockchain in Cybersecurity.





