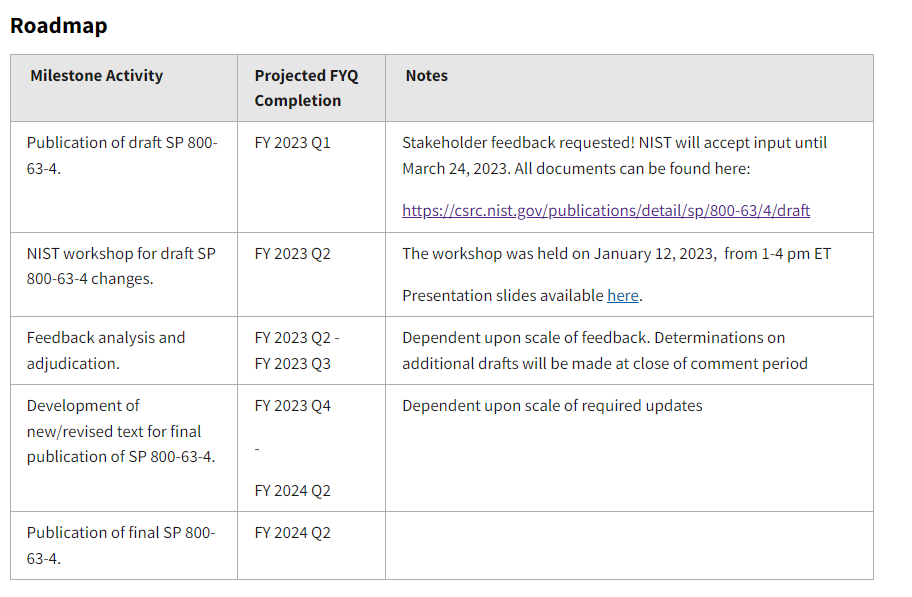
In December 2022, the fourth draft of the NIST Digital Identity Guidelines (SP 800-63 4) was published. NIST has requested comments on the fourth draft revision by March 24, 2023. The process and technical requirements for meeting the digital identity management assurance levels specified in each volume are presented in this publication.
They also propose ways to enhance the privacy, equity, and usability of digital identification systems and technologies.
In this article, we outline key requirements from NIST and how the use of a Public Key Infrastructure becomes a necessary requirement in order to adhere to these Guidelines.
Genuine Identity vs. Digital Identity
Every person and "entity" (computers, smartphones, internet-connected devices (IoT), applications and further endpoints) in today's digital environment has a unique digital identity. A digital identity contains certain unique identifiers that allow systems, services, and applications to know who or what they are interacting with. To verify a person's identity in the digital world and without human intervention, a combination of data and attributes is required to validate an identity.
A digital identity does not necessarily uniquely identify a person in all settings, but it is always identifiable within the context of a digital service. The genuine identity of the person behind a digital identity might not be known, even while it may convey a distinct and distinctive meaning within the context of a digital service.
So, a digital identity is a representation of a real person, made up of unique identifiers or attributes. These identifiers could be a driving license number, an email address, or a passport number.
There are also instances where the association with a real-life subject is needed by legislation (for example, the financial industry's "Know Your Customer" standards) or to establish accountability for high-risk acts.
The purpose of establishing a digital identity is to establish trust between the identity holder and the person, organization, or system executing the digital transaction. It is important that organizations relying on digital identities adopt a robust set of procedures to determine whether an individual is who they say they are. This is particularly important when using online services where the strength of the evidence is paramount. Therefore, NIST has established these Digital Identity Guidelines which allow for certain types of evidence and methods of grading to determine the strength of the resulting assured digital identity.
NIST Key Recommendations for Identity Proofing
Here we look at the key recommendations that provide technical guidelines to organizations for the implementation of digital identity services.
1. Digital Identity Model
The SP 800-63 guidelines use digital identity models that reflect technologies and
architectures currently available in the market. These models have a variety of entities
and functions and vary in complexity. Simple models group various functions, such as creating subscriber accounts and providing attributes, under a single entity. More complex models separate these functions among a larger number of entities. The entities and their associated functions found in digital identity models include:
- Applicant - the subject to be identity proofed.
- Subscriber - the subject that has successfully completed the identity proofing process or has successfully completed authentication.
- Claimant - the subject to be authenticated.
2. Expected Outcomes of Identity Proofing
The expected outcomes of identity proofing include:
- Identity resolution: determine that the claimed identity corresponds to a single, unique individual within the context of the population of users the Credential Service Provider (CSP) CSP serves;
- Evidence validation: confirm that all supplied evidence is genuine, authentic, and unexpired;
- Attribute validation: confirm the accuracy of core attributes;
- Identity verification: verify that the claimed identity is associated with the real-life person supplying the identity evidence;
- Fraud Prevention: mitigate attempts to gain fraudulent access to benefits, services, data, or assets.
3. Establishing strong identity-proofing processes to ensure that only legitimate users are able to access digital systems and resources
NIST feels that an unattended, fully remote Identity Assurance Level (IAL) 2 identity proofing workflow that provides security and convenience but does not need facial recognition should be included.
Within draft NIST SP 800-63A-4, an outline is provided detailing the basic flow for remote identity proofing and enrollment:
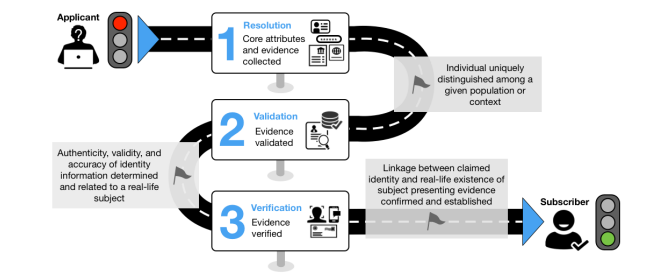
Source: NIST Special Publication
4. Evidence Validation & The Role of the Credential Service Provider
A Credential Service Provider (CSP) is a trusted entity whose functions include identity-proofing applicants to the identity service and the registration of authenticators to subscriber accounts. A CSP may be an independent third party.
Identity Resolution
The CSP SHALL collect evidence from the applicant according to one of the following options:
- Two pieces of SUPERIOR evidence,
- One piece of SUPERIOR evidence and one piece of STRONG evidence,
- Two pieces of STRONG evidence and one piece of FAIR evidence.
Superior evidence (4.3.3.3)
In order to be considered SUPERIOR, identity evidence SHALL meet all the following
requirements:
- The issuing source of the evidence confirmed the claimed identity by following written procedures designed to enable it to have high confidence that the source knows the real-life identity of the subject. Such procedures are subject to recurring oversight by regulatory or publicly accountable institutions.
- The issuing source visually identified the applicant and performed further checks to confirm the existence of that person.
- The issuing process for the evidence ensured that it was delivered into the possession of the person to whom it relates.
- The evidence contains at least one reference number that uniquely identifies the person to whom it relates.
- The evidence contains a facial portrait or other biometric characteristics of the person to whom it relates.
- The evidence includes digital information that is cryptographically signed.
- The evidence includes physical security features that make it difficult to copy or reproduce.
- The evidence includes an expiration date and is unexpired.
In the instance of one of the points above, ‘digital information that is cryptographically signed’ refers to the use of a digital signature. A digital signature is a method for secure authentication of digital documents or messages, based on asymmetric cryptography. Using a Public Key Infrastructure (PKI) enables the required evidence containing cryptographically signed digital information by using public-private key pairs to create and issue digitally signed certificates to the entities. It therefore provides proof for the entity confirming the validation of its identity.
Strong evidence (4.3.3.2)
In order to be considered STRONG, identity evidence SHALL meet all the following
requirements:
- The issuing source of the evidence confirmed the claimed identity through written procedures designed to enable it to form a reasonable belief that it knows the real-life identity of the person. Such procedures are subject to recurring oversight by regulatory or publicly-accountable institutions. For example, the Customer Identification Program guidelines established in response to the USA PATRIOT Act of 2001 or the [RedFlagsRule], under Sec. 114 of the Fair and Accurate Credit Transaction Act of 2003 (FACT Act).
- There is a high likelihood that the evidence-issuing process would result in the delivery of the evidence to the person to whom it relates.
- The evidence contains a reference number or other attributes that uniquely identify the person to whom it relates.
- The evidence contains a facial portrait or other biometric characteristic of the person to whom it relates.
- The evidence includes physical security features that make it difficult to copy or reproduce.
- The evidence includes an expiration date and is unexpired.
Fair evidence (4.3.3.1)
In order to be considered FAIR, identity evidence SHALL meet all the following
requirements:
- The issuing source of the evidence confirmed the claimed identity through an identity proofing process.
- It can be reasonably assumed that the evidence issuing process would result in the delivery of the evidence to the person to whom it relates.
- The evidence contains at least one reference number, a facial portrait, or sufficient attributes to uniquely identify the person to whom it relates.
- The evidence has not expired or it expired within the previous six (6) months, or it was issued within the previous six (6) months if it does not contain an expiration date.
Evidence Validation
A CSP is required to validate all evidence collected to meet evidence collection requirements and all core attribute information that is required by the CSP identity service.
The CSP SHALL validate the genuineness of each piece of SUPERIOR evidence by
confirming the integrity of its cryptographic security features and validating any digital signatures.
The CSP SHALL validate the genuineness of each piece of STRONG evidence by one of the following:
- Visual inspection by trained personnel,
- The use of technologies that can confirm the integrity of physical security features and detect if the evidence is fraudulent or has been inappropriately modified,
- If present, confirming the integrity of digital security features, including the validity of the issuer’s digital signature.
The authenticity and accuracy of identity evidence or attribute information that is cryptographically protected can be validated through verification of the digital signature on the evidence or the attribute data objects. The CSP SHALL use the public key of the issuing authority of the evidence to verify digitally signed evidence or attribute data objects.
One of the points above, ‘confirming the integrity of digital security features, including the validity of the issuer’s digital signature’ refers to the secure creation and issuance of digital certificates, signed by the Certification Authority (CA) as the core element of a PKI, and issued to the entity. In order to ensure highly secure generation of the private-public key pairs issued as the base for the certificate creation and issuance to the individual entities, a Hardware Security Module (HSM) is, therefore, a necessity for key generation in accordance to the highest security standards. HSMs act as the trust anchor for the identity of the entities as such as well as the certificates issued by the public key infrastructure.
Authenticators SP 800-63 4
The classic paradigm for authentication systems identifies three factors as the
cornerstones of authentication:
- Something you know (e.g., a password)
- Something you have (e.g., an ID badge or a cryptographic key)
- Something you are (e.g., a fingerprint or other biometric characteristic data)
Authentication Process (4.3.4.1)
The CSP SHALL validate the authenticity, accuracy, and currency of presented evidence
by:
- Confirming the evidence is in the correct format and includes complete information
- for the identity evidence type.
- Confirming the evidence is not counterfeit and that it as not been tampered with.
- Confirming any security features.
The CSP SHALL validate that the evidence is current through confirmation that its
expiration date has not passed or that evidence without an expiration date was issued within the previous six (6) months.
The authenticity and accuracy of identity evidence or attribute information that is
cryptographically protected can be validated through verification of the digital signature on the evidence or the attribute data objects. The CSP SHALL use the public key of the issuing authority of the evidence to verify digitally signed evidence or attribute data objects.
Evidence and Attribute Validation Methods
4.3.4.3 Acceptable methods for validating presented evidence include:
- Visual and tactile inspection by trained personnel for in-person identity proofing,
- Visual inspection by trained personnel for remote identity proofing,
- Automated document validation processes using appropriate technologies,
- Validation of attributes contained on the evidence with an authoritative or credible source.
- Verification of the digital signature protecting digital evidence or attribute data objects using the public key of the issuing authority of the evidence.
In all instances of Evidence Validation, Public Key Infrastructure (PKI) becomes a major requirement. They work as enablers for trust relationships among the certified entities, confidentiality in their communication and integrity of data generated and exchanged by them.
Conclusion
Digital transformation is a key driving force behind the adoption of digital identities. The importance of Public Key Infrastructure (PKI), the technology behind digital certificates, fulfills a similar purpose similar to a driving license or passport - a digital certificate functions similarly to a driver's license or a passport in that it is a piece of identification that validates your identity and provides you specific privileges.
The NIST Guidelines make a strong reference throughout as to how PKI is considered to be a ‘trust enabler’ and be used to authenticate identities. By proving ownership of a private key, PKI provides a trust service that can be used to verify that the sender or receiver of information is exactly who they claim to be.
As NIST Guidelines detail and explain the necessity of using a PKI, introducing a PKI into an organization requires certain planning, procedures, and deployment. Any effective security strategy must include identity security as a key component. Find out how Utimaco’s solutions can become an ideal solution for your requirements.