Meeting the Cybersecurity Requirements of the NIS2 Directive
The Directive (EU) 2022/2555 of the European Parliament and of the Council – also known as the NIS2 Directive (Network and Information Systems Directive) – is a regulatory framework to raise the level of cybersecurity of networks and information systems across the EU, and was announced in December 2022.
Its predecessor, the 2016 NIS Directive (Directive (EU) 2016/1148 of the European Parliament and of the Council), already required certain industries to take appropriate measures for their cybersecurity and incident reporting.
What’s new in NIS2:
- The broader scope of sectors
- Stronger and more explicit cybersecurity obligations
- Includes more governance and accountability for organizations cybersecurity
- Addresses cybersecurity of the supply chain and third parties
- Includes cyber incident reporting requirements
The full text of the Directive can be found here
Redefining the importance of cybersecurity in the EU
With the NIS2 Directive, the EU Parliament aims to increase the level of cyber resilience. They identified an inconsistent level of resilience across the Member States and sectors, as well as a lack of common understanding of the main threats and challenges, and a shortcoming of common crisis response. Therefore, the revised Directive incorporates legal measures to increase the overall cybersecurity level in the EU and shall be transposed into national law.
When will the NIS2 Directive enter into force?
It is planned that the NIS2 Directive will be transposed into national law across EU Member States on 18 October 2024.
Who will be affected by the NIS2 Directive?
The measures will be applicable to all entities which (i) provide their services or carry out their activities in the EU, and (ii) match the description of either an “essential” or an “important” entity in a defined list of sectors.
The NIS2 Directive includes entities of high criticality, such as:
- Energy
- Transport
- Banking
- Financial market institutions
- Health
- Public administration
And more; see the full list of sectors here
How Utimaco’s cybersecurity solutions help you comply with the NIS2 Directive
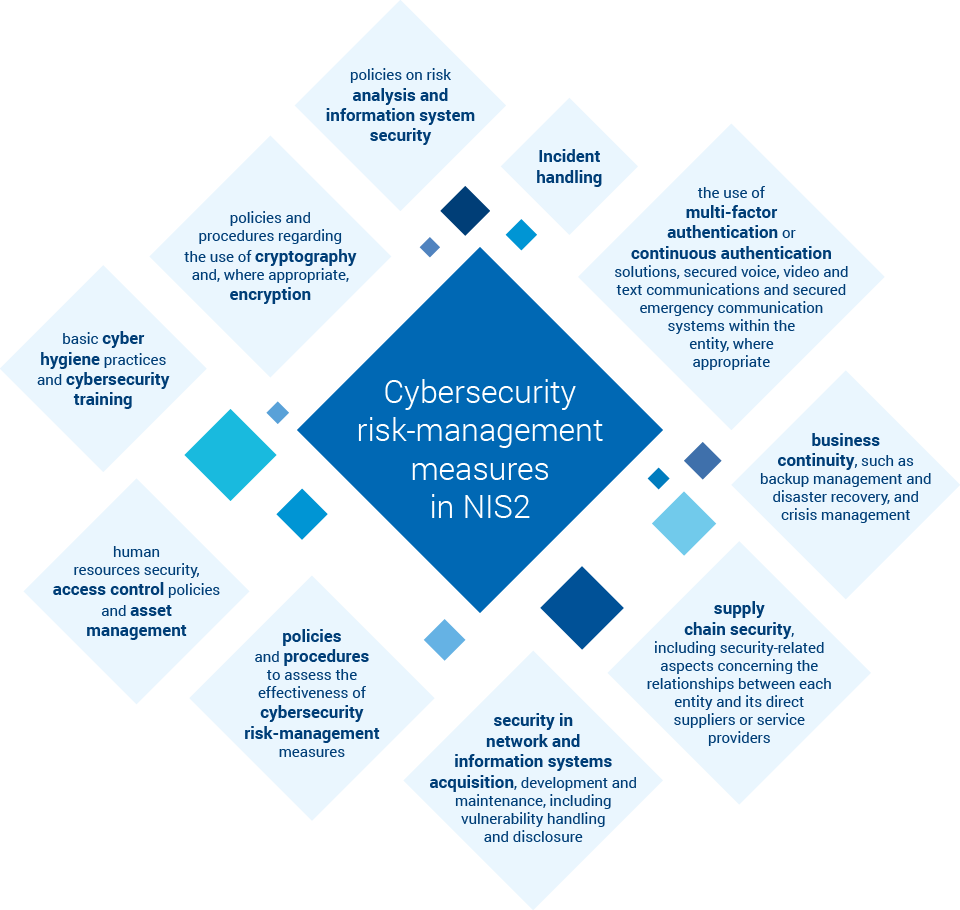
Utimaco supports and welcomes the NIS2 Directive. Our cybersecurity solutions help you in preparing to meet the cybersecurity-related requirements defined in Article 21 of the NIS2 Directive.
Among others, these include the following measures:
- Supply chain security
- […] the use of cryptography and, where appropriate, encryption
NIS2 highlights the importance of cryptography
Cryptography has been in our DNA for over 40 years. Our hardware security modules enable organizations to implement cryptographic security for a wide range of business applications. In addition to this, we offer key management, encryption software, and Public Key Infrastructure for a complete (data) protection portfolio.
We enable organizations to build a trusted cybersecurity infrastructure in compliance with NIS2. Comply with NIS2 - and the upcoming federal laws - with a focus on:
Data Protection
Protect sensitive personal and organizational data – regardless of the storage location.
Trusted Processes
Establish trust throughout your supply chain with identity management and continuous auditing of all involved entities.
Cryptography and Encryption
Implement additional cryptographic operations as needed, based on your infrastructure.















