The quantum clock is ticking. By 2030, certain asymmetric algorithms will be deprecated by NIST — and by 2035, they’ll be fully disallowed. It's already mid-2025, and that once-distant deadline is fast approaching. Instead of complaining like the White Rabbit from Alice in Wonderland, exclaiming “Oh dear! Oh dear! I shall be too late!”, it’s time to prepare with confidence.
To help you stay ahead, here are five essential steps to successfully navigate your migration to post-quantum cryptography (PQC).
Step 1: Crypto Discovery – Look beyond your use cases
Before embarking on a major initiative like post-quantum cryptography migration, it's crucial to understand your current cryptographic landscape. Since PQC requires replacing vulnerable algorithms like RSA and ECC, you need to know where and how these algorithms are used across your organization.
This is where crypto discovery comes in.
Crypto discovery is the process of building a comprehensive cryptographic inventory — a detailed audit of your systems that includes keys, certificates, algorithms, libraries, and protocols. By gaining full visibility into your cryptographic assets, you establish a clear picture of your current security posture.
A successful crypto discovery initiative should uncover all cryptographic elements in your environment, including:
- Protocols
- Libraries
- Algorithms
- Certificates
- Keys
But don’t stop at internal systems. It’s just as important to examine third-party software used in your organization. Tools and frameworks like SBOM (Software Bill of Materials) and CBOM (Cryptographic Bill of Materials) are invaluable for identifying and documenting cryptographic components in external dependencies.
Learn more about the role of SBOM and CBOM in PQC migration here.
A complete cryptographic inventory lays the foundation for every step that follows in your PQC journey.
Step 2: Risk Analysis – Prioritize your use cases
Migrating everything, everywhere, all at once might work for Michelle Yeoh — but in PQC migration, it’s a recipe for chaos. A more effective strategy is to migrate use case by use case, based on a clear risk assessment.
Conducting a structured risk analysis will help you determine where to start and how to prioritize your efforts. Here's how:
- Break down the migration process by individual use cases (e.g., systems, applications, or products)
- Assess the lifespan of each use case — how long will it be active and exposed?
- Estimate migration timelines — how long will it take to transition each one?
- Evaluate severity and impact — what’s the security level and sensitivity of each use case?
- Summarize and rank use cases based on urgency, complexity, and risk
By identifying high-risk or long-lived systems first, you can focus your resources where they matter most — ensuring a smoother, more secure PQC transition.
Step 3: Plan and execute - Test the algorithms
Transitioning from classical to post-quantum cryptographic algorithms isn’t a simple 1:1 swap — there’s no universal blueprint. The right PQC algorithm for your organization depends on multiple factors, such as:
- Required performance and latency
- Available memory and resource constraints
- Implementation strategy (full PQC vs. hybrid)
- System architecture and environment
- Existing applications and integration needs
The only reliable way to make informed decisions is through hands-on testing. Simulate PQC algorithms in your actual environment to evaluate performance, compatibility, and integration — not just in theory, but under real-world conditions.
To support this, Utimaco’s free Quantum Protect Simulator enables your development teams to test NIST- and BSI-recommended algorithms — including both lattice-based and hash-based cryptography — directly within your systems.
This testing phase is key to identifying the best-fitting solutions before full-scale deployment.
Step 4: Protect PQC keys – use hardware-based security
No matter the algorithm, cryptographic keys are only as secure as the environment that manages them. This holds true for post-quantum cryptography (PQC) as well. To ensure the highest level of protection, keys should be generated, stored, and managed within a trusted hardware-based environment.
The most secure solution is a Hardware Security Module (HSM).
An HSM generates keys using a built-in true random number generator, ensuring high entropy and strong key material. It then securely stores those keys within a tamper-resistant, isolated environment, where private keys never leave the module — safeguarding them from exposure or compromise.
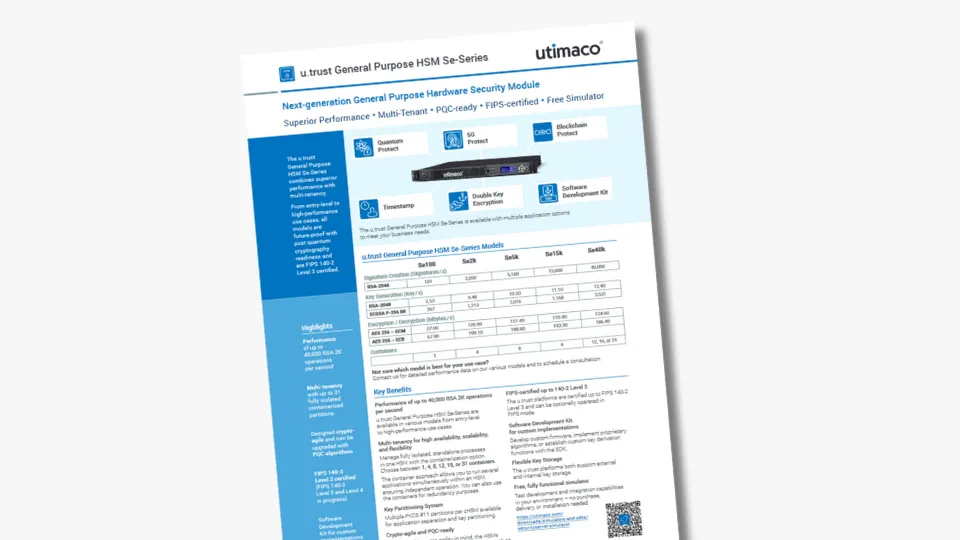
Utimaco’s u.trust General Purpose HSM Se-Series is designed crypto agile and can be upgraded with NIST-standardized PQC algorithms already today. It is available on-premises or as a service, giving you flexibility without compromising security.
Step 5: Future-proof your systems - embrace crypto-agility
A crypto-agile system is one that allows cryptographic components — such as algorithms, keys, or protocols — to be updated or replaced without compromising security or disrupting operations. It includes having well-defined procedures in place to make these changes smoothly and securely.
In the context of post-quantum cryptography, crypto-agility is more important than ever.
Many PQC algorithms are still relatively new and lack the decades of real-world testing that classical algorithms like RSA or ECC have undergone. As these algorithms evolve, updates or changes may be mandated by standards bodies like NIST.
By designing your systems to be crypto-agile, you ensure:
- Easier adaptation to future updates or vulnerabilities
- Seamless algorithm replacement without security gaps
- Long-term flexibility as cryptographic standards evolve
Don’t just migrate — future-proof. Crypto-agility is your key to staying secure and compliant in a rapidly changing cryptographic landscape.