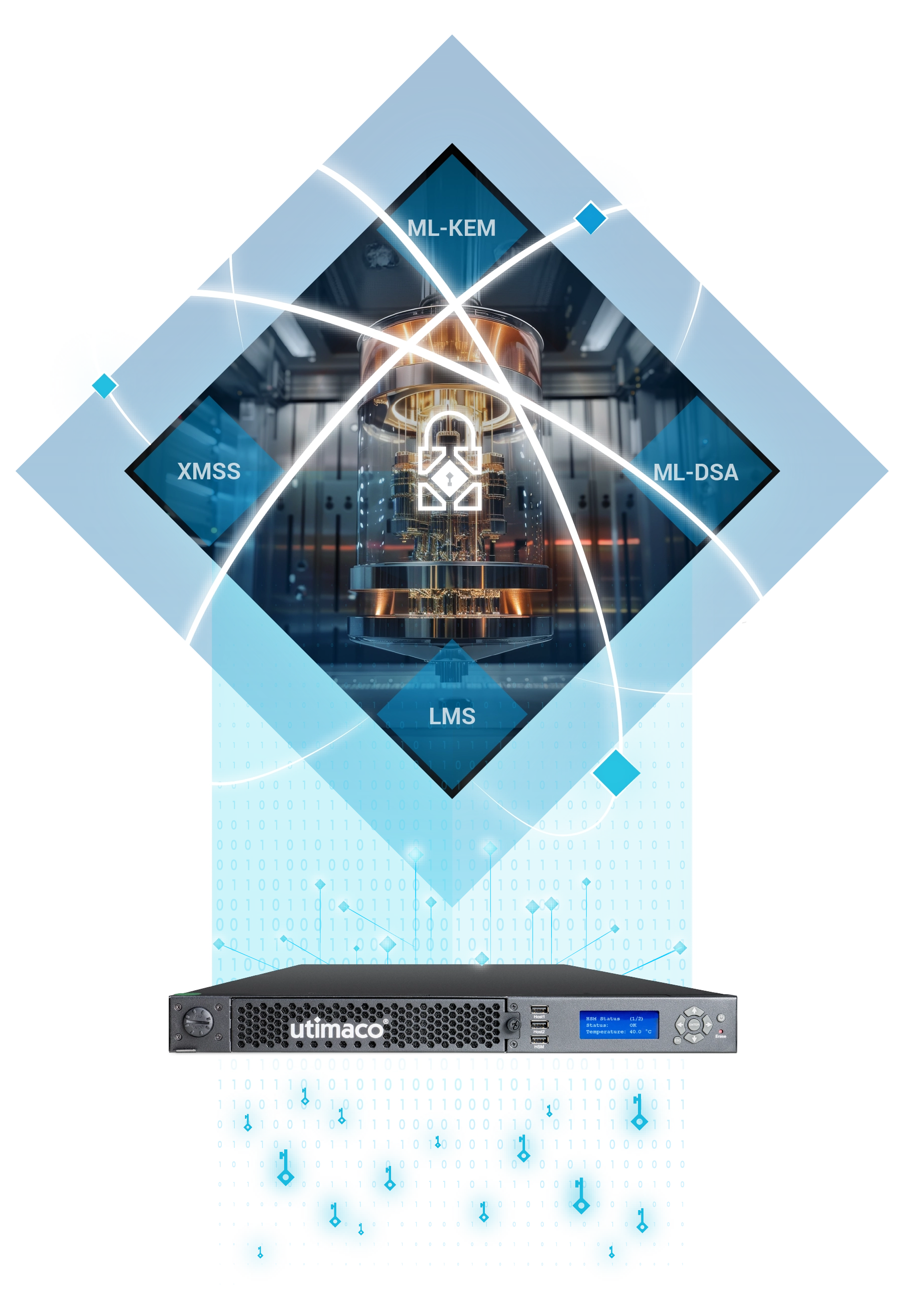
使用例

Utimacoソリューションを選ぶメリット

Utimacoとは長い間、プライベート・プロジェクトでも一緒に仕事をしており、様々な良い経験を積んできました。例えば、私たちはUtimaco HSMと共に可用性の高いソリューションを開発し、エネルギー市場に提供しています。
メディア・トランスファーAG CEO
ケーススタディを見るUtimacoが特に気に入っている点は3つあります。柔軟性、ポートフォリオの包括性、協調性、そして暗号通貨ビジネスのような業界では重要な顧客サービス、そしてもちろんUtimacoが世界中に示している信頼です。
フィノア共同創業者兼マネージング・ディレクター
ケーススタディを見るUtimacoと仕事をするのが好きなのは、社風がとても合っているからだ。非常にオープンで、サポートが非常によく、質問の多くは技術的なもので、私たちのエンジニアはUtimacoのエンジニアと協力して顧客の問題を解決しています。
スウェーデンNexus Group CEO
ケーススタディを見る私たちは暗号の専門家ではないので、Utimacoと仕事をするのがとても好きです。しかし、私たちが顧客にソリューションを提供する場合、セキュリティや暗号化というトピックは通常、全体的なソリューションの一部なので、同じビジョンを共有する専門家に頼ることになります。
Diebold Nixdorf
ケーススタディを見る成功をシミュレートする
HSMシミュレータで、当社のハードウェア・セキュリティ・モジュールとアプリケーション・パッケージの機能をテストし、評価することができます。今すぐアカウントを作成して、旅を始めましょう。
パートナー
エコシステム
すべて見る
同業者がPQCへの移行をどのように進めているかを知り、Utimacoの暗号化専門家から実践的な知見を得ましょう
決済セキュリティを最高水準へ引き上げる準備はできていますか?
あなたの未来を守る準備はできていますか?
データ保護、Key管理、セキュアな決済、コンプライアンス・ソリューションなど、オンプレミスおよびAs-a-Serviceの包括的なポートフォリオをご覧ください。
お問い合わせ