As discussed in our previous blog post: NIST has finally released the first three standards for Post Quantum Cryptography (PQC) this year:
- ML-KEM (FIPS-203)
- ML-DSA (FIPS-204)
- SLH-DSA (FIPS-205)
Now that the standards are published, a question arises: How to comply with these standards and where to start migrating? While these new standards mark the beginning of a new era in cryptography, the journey from them to widespread adoption is neither immediate nor straightforward.
In this blog post, we’ll explore the complexities of integrating quantum-safe algorithms across the software supply chain.
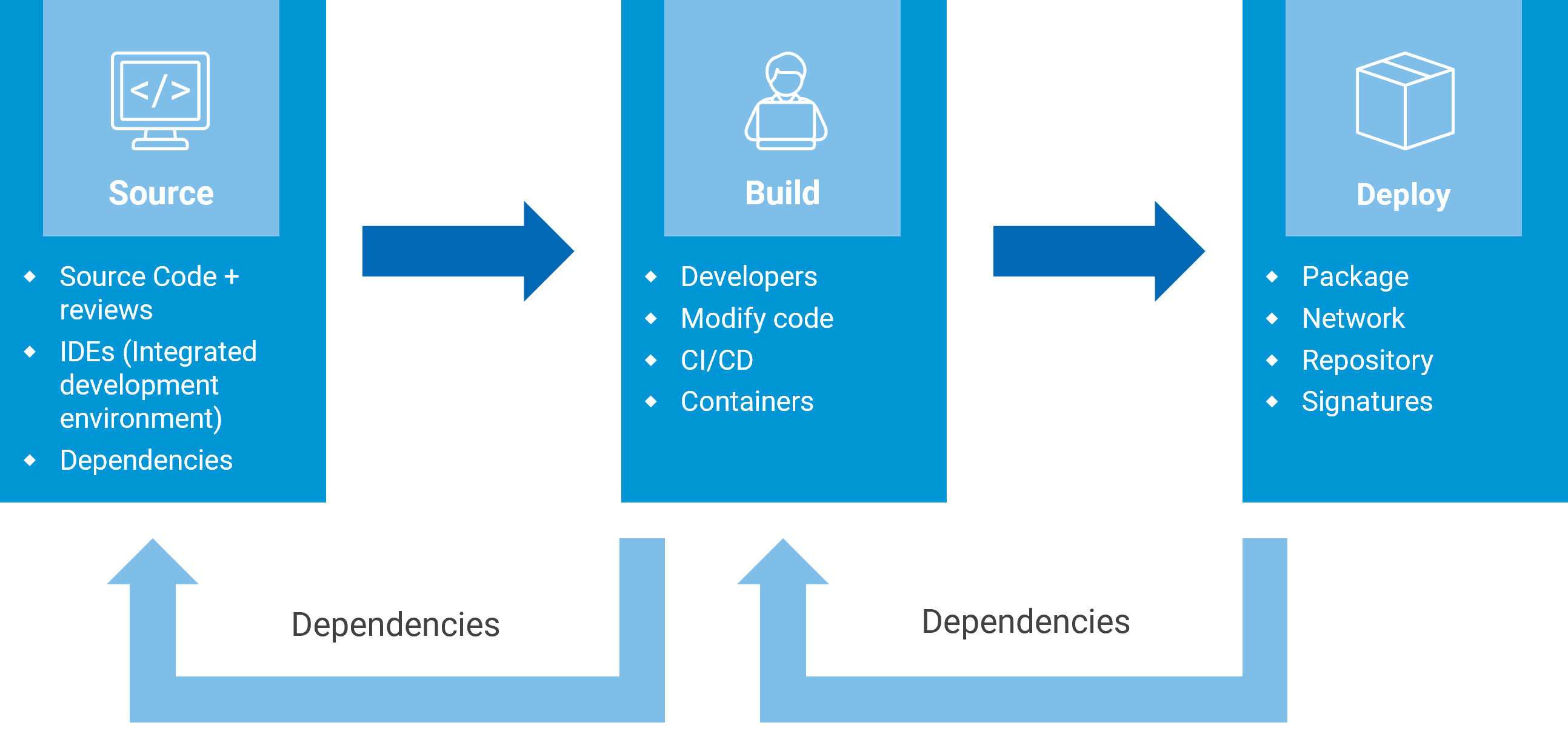
Software Supply Chain: What It Is and Its Role in Security Vulnerabilities
In software development, it is very common to rely on existing software, such as open-source libraries, developer tools, and other software products. These pieces are integrated into an extensive supply chain that includes all aspects of the IT infrastructure, such as hardware, source code, third-party tools, platforms, data storage, and testing and distribution systems. .
The importance of the software supply chain is particularly apparent when it comes to zero-day exploits. For example, in December 2021, a serious vulnerability was discovered in the widely used open-source Java library Log4j. The widespread use of Log4j in numerous Java applications, combined with the lack of visibility into where it was implemented, triggered a global scramble among software vendors and IT departments to assess their systems for potential exposure. Having a software component with a vulnerable version of Log4j provided an entry point for attackers, impacting the security of the entire supply chain.
What is a Software Bill of Materials (SBOM)?
SBOM stands for Software Bill of Materials. It provides a detailed list of all the software components that make up a product's codebase. Whether it is a device, software, or service, it details everything from libraries and modules to dependencies, offering visibility into what the product is built from.
An SBOM typically includes:
- Software components
- Supplier name
- Software version
- Other unique identifiers
- Software relationships and dependencies
- Author
- Timestamp
The importance of the software supply chain is particularly apparent when it comes to zero-day exploits, as the information provided by the SBOM becomes a crucial tool in managing and mitigating these vulnerabilities.
Product owners can directly check whether a product relies on the affected software or open-source libraries with known vulnerabilities by reviewing the SBOM and the underlying license and version information.
The Software Bill of Materials (SBOM) helps identify and resolve software vulnerabilities.
The road to PQC adoption: Who is the first link in the software supply chain?
For private sector organizations, the transition to post-quantum cryptography is a complex process that goes beyond a simple software upgrade. The real challenge is ensuring that the entire software supply chain is quantum secure. From libraries to protocols to cryptography, every link in the chain must adapt to ensure security in the quantum age.
The goal of a software bill of material is to increase the transparency of the software used in certain products, thereby increasing cyber resilience by making it much easier to track and fix emerging vulnerabilities.
Wouldn't it be useful to have a similar list for cryptography, so that you can immediately see what kind of classical algorithms you rely on and where you should switch to post-quantum cryptography sooner rather than later? This would help you identify and address potential risks before they become critical.
Fortunately, such a tool already exists: the Cryptographic Bill of Materials (CBOM).
What is Cryptography Bill of Materials (CBOM)?
CBOM stands for Cryptography Bill of Materials and is an extension to the SBOM.
A CBOM would contain information about:
- Cryptographic assets
- Cryptographic properties
- Cryptographic dependencies
- Related cryptographic material (type, size, format, secured9
- Certificates
- Algorithms
- Security Level (+Quantum Security Level!)
With the CBOM at hand, organizations will find it much easier to scan, discover, and manage the cryptography and algorithms used in their products, software, services, and infrastructure.
The Cryptography Bill of Materials (CBOM) helps identify priorities and security gaps for PQC migration.
Implementing post-quantum cryptography is much easier if you know your crypto
The transition to the new Post-Quantum Cryptography standards presents several challenges. Although the basic algorithms have been standardized, the private sector, particularly enterprises, will face a waiting period before these algorithms are fully implemented in various protocols, standards, and the libraries that support them, as well as the products that rely on these libraries. This process requires a development chain, with cryptographic product developers and product vendors expected to be the first adopters of these standards.
For enterprises, this transition will also involve the use of third-party products, underscoring the importance of maintaining a comprehensive software bill of materials and cryptography bill of materials. In addition, orchestrating the entire supply chain to ensure it is in a quantum-safe state is critical.
As we move into the era of post-quantum cryptography, it is becoming increasingly clear that understanding and managing the cryptographic elements within your software ecosystem is critical. Having a well-maintained software supply chain, as well as SBOMs and CBOMs, provides organizations with the visibility they need to effectively adapt to PQC.
For organizations without an up-to-date SBOM or CBOM, using a crypto discovery tool can be a critical first step in gaining visibility into the cryptographic landscape of their systems.
How Utimaco helps you with PQC transition
Utimaco's partnership with Infosec Global is an example of a forward-thinking approach to this challenge. Through this collaboration, we provide integration with their crypto discovery tool, AgileSec Analytics, which helps you build a complete inventory of protocols, libraries, algorithms, certificates and keys. In combination with Utimaco's Crypto Agile Hardware Security Modules (HSMs), organizations are well equipped for the post quantum era.
Utimaco’s firmware extension Quantum Protect already upgrades our HSMs with Post Quantum Cryptography algorithms such as LMS and XMSS, which are requested by the CNSA 2.0 for software and firmware signing. In addition, it provides pre-standard versions of ML-KEM (Crystals-Kyber) and ML-DSA (Crystals-Dilithium), with final standards on our roadmap. Best of all, there's no need to replace your hardware; our devices are upgradeable in the field through seamless firmware upgrades.
We are pleased that these efforts are being recognized by the market - not only by the customers who are already using our PQC solutions, but also by the Frost & Sullivan Strategy Leadership Award!

By adopting these strategies and tools, organizations can confidently navigate the transition to PQC, ensuring that their cryptographic infrastructure remains robust, future-proof, and ready for the quantum age.







