In the dynamic landscape of digital information, maintaining an indisputable chronology of document creation, proof of its unaltered state since its creation, and ongoing digital modifications presents a critical challenge.
Timestamping has emerged as a robust solution, addressing the need for secure and unalterable documentation. At its core, this process involves securely recording the exact creation and modification times of a document, establishing a timeline that remains resistant to tampering.
In this article, we delve deeper into the realm of electronic timestamping, where security meets chronology to fortify the foundation of digital trust.
What is Electronic Timestamping?
Timestamping is a process that involves assigning a specific date and time to events, data, or documents, providing a chronological reference for when they occurred. In the digital realm, timestamping is fundamental for ensuring data integrity, authenticity, and accountability. It functions as a chronological ‘stamp’, capturing the moment an action takes place and facilitating verification of the information's accuracy.
Timestamps play a vital role in maintaining data integrity because they allow users to track modifications or changes made to a document or data over time. Implementing timestamping for electronic signatures is critical for ensuring data integrity and establishing a credible timeline for digital transactions.
Electronic timestamping is a process whereby a date and time can be electronically bound to other data in electronic form to certify, of its existence or execution at a given moment, and also to attest to its content at that precise time.
When is electronic timestamping required?
Electronic Timestamping is used in a variety of situations where establishing a precise chronological order and recording the timing of events or data is critical. This is particularly crucial in fields where the accuracy and security of digital documents hold paramount importance, such as legal documentation, invoicing, artistic creation, or any domain reliant on trustworthy digital records.
Some typical scenarios where timestamping is required include:
Legal Documents: Timestamps are frequently required in contracts, agreements, and intellectual property filings. They provide a verifiable record of when the document was created and signed, which can be advantageous during legal disputes.
Digital Signatures: Timestamps are essential when using digital signatures to sign electronic documents. They ensure that the signature remains immutable, valid and was applied at a specific point in time, providing the reliable proof of authentication.
Data Integrity: Timestamps are used to ensure the integrity of data over time. By associating a timestamp with a dataset or document, users can keep records of any changes or modifications, ensuring information accuracy and reliability.
Financial Transactions: Timestamping is utilized in the financial industry to record the timing of transactions. It assists in auditing, compliance, and dispute resolution by establishing the sequence of financial events.
Regulatory Compliance: Many industries, particularly those subject to regulatory oversight, require timestamping to meet legal and regulatory requirements. This is common in banking, healthcare, insurance, lottery and gaming, as well as other industries where accurate record-keeping is required.
Contractual Services: Timestamps play a role in documenting when specific services were initiated, completed, or modified, providing a verifiable record for contractual agreements. This can be crucial for billing, auditing, and dispute resolution purposes.
Emergency Services & Response Time Documentation: Timestamping is used for emergency services, such as fire departments and ambulances, to document and confirm the time of dispatch, arrival at the scene, and response completion. This data is essential for determining the effectiveness of emergency response strategies, guaranteeing responsibility, and possibly implementing changes to improve public safety.
Authentication and Security: Timestamping enables security systems to enhance their resilience against potential threats, ensuring the integrity and trustworthiness of cryptographic operations. Timestamping is also used in access logs and security auditing to track when users access systems or databases.
Supply Chain Management: Timestamping is used to record the timing of various events such as shipments, deliveries, and inventory movement. This helps with traceability, transparency, and accountability.
Digital Forensics: Timestamps play an important role as they establish a timeline of events in electronic investigations. They assist investigators in reconstructing the sequence of events on digital devices.
Timestamping is essential whenever there is a need for a precise record of when an event occurred or when data was created or changed for operational, legal, security, or compliance-related purposes.
How does Timestamping work?
The following process is used in timestamping scenarios where strong authentication, data integrity and long term validity are essential, such as in the use cases described earlier. In this instance, hash signing with a timestamp certificate is a process that involves creating a digital signature for a hash value of electronic data and then appending a timestamp to the signature.
The combination of digital signature and timestamp serves several purposes, including ensuring data integrity, providing non-repudiation, and establishing a verifiable record of when the signature was applied.
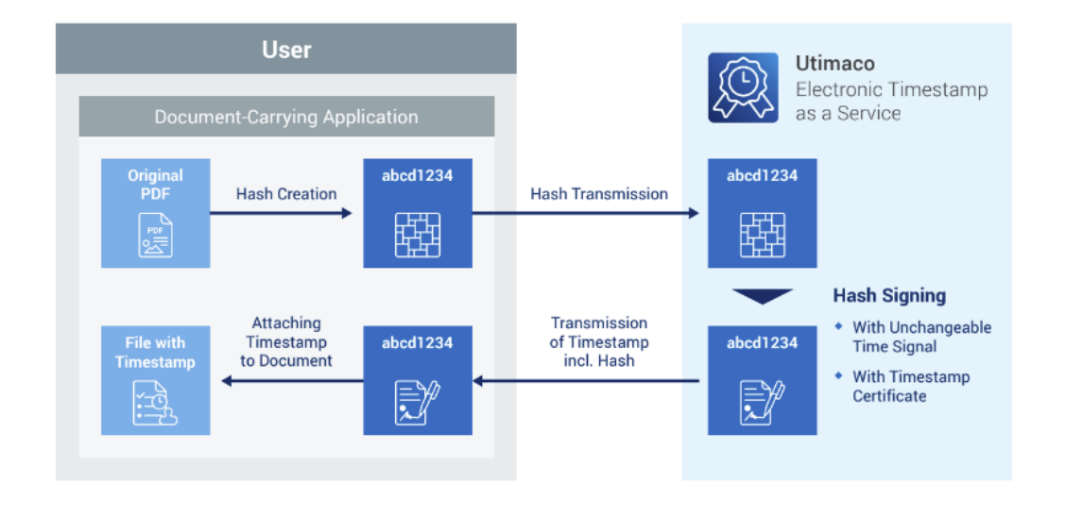
The key components of the steps involved in the process include:
Hash Creation: The process begins with creating a hash value of the electronic data using a cryptographic hash function (e.g., SHA-256). The hash value is a fixed-size string of characters unique to the input data.
Private Key Signing: The hash value is then signed using the private key of the entity generating the signature. This creates a digital signature that is unique to both the hash value and the private key.
Timestamping: To enhance the long-term validity of the digital signature, a timestamp is obtained). This timestamp indicates the exact time when the signature was applied.
Combining Signature and Timestamp: The digital signature and the timestamp are combined and appended to the original electronic data or document. This creates a single entity that includes the hash value, digital signature, and timestamp.
Timestamp Verification: The timestamp can be independently verified by checking with the trusted Timestamp Authority. This confirms the time at which the signature was applied, adding an extra layer of assurance regarding the temporal aspect of the signed data.
The creation of timestamps need to be conducted in a highly secure and certified environment that adheres to rigorous standards, notably ISO 27001. ISO 27001 is an international standard that outlines best practices for information security management systems (ISMS). Achieving ISO 27001 certification signifies that a comprehensive set of security controls and processes have been met in order to ensure the confidentiality, integrity, and availability of information. ISO 27001 is particularly relevant in the realm of information security and data protection.
Timestamping as a Service - Elevating Efficiency and reducing Total Cost of Ownership
Implementing Electronic Timestamp as a Service involves leveraging a digital solution that frees organizations from on-premises infrastructure costs. This service offers a dynamic and flexible approach, allowing for seamless upscaling or downscaling based on specific needs.
Organizations can efficiently manage their timestamping requirements without the burden of maintaining physical infrastructure. This flexibility not only ensures cost-effectiveness but also allows organizations to adapt their timestamping capabilities to evolving demands, enhancing accessibility, scalability, and cost-efficiency.
Benefits:
Streamlined Setup: Easily established without the need for technical expertise
Document & Data Integrity: Timestamping creates an immutable record of the exact time when a document or piece of data is created or modified. This timestamp serves as a digital seal, making it evident if any unauthorized alterations have occurred after the timestamp was applied.
Verification of Authenticity: The timestamping process, coupled with cryptographic techniques, provides a means to verify the authenticity of documents and data. Recipients can use the timestamp information to confirm that the content has not been forged or manipulated.
Protection Against Data Corruption: Timestamping provides an additional layer of protection against data corruption. In the event of accidental or deliberate data corruption, the timestamped records can be used to determine the state of the data at the time of the timestamp.
Legally Admissibility: Timestamped documents often hold greater weight in legal proceedings. The timestamp serves as a reliable chronological record, enhancing the admissibility and credibility of digital evidence in legal contexts.
SaaS Efficiency: Operates on a Software as a Service (SaaS) model, entrusting Utimaco with the comprehensive management of maintenance, security protocols, and audits.
Reduction in Total Cost of Ownership (TCO): Electronic Timestamp as a Service can contribute to a reduction in TCO for organizations by optimizing resource allocation, minimizing infrastructure costs, and streamlining operational efficiency. Benefits include:
- Infrastructure Cost Savings - Utilizing a cloud-based Timestamp as a Service eliminates expenses tied to maintaining on-premises servers, hardware, and dedicated IT staff for timestamping.
- Scalability Efficiency: Efficient scaling of timestamping capabilities, aligning resources with demand.
- Automated Updates and Maintenance- Updates and maintenance tasks are updated automatically, reducing the need for internal IT teams to manage manual software updates and system maintenance.
- Reduced IT Overhead - Decreases reliance on in-house IT personnel dedicated to managing a timestamping infrastructure, leading to cost savings on salaries and benefits.
- Enhanced Business Continuity - A cloud-based service with high availability and business continuity features reduces downtime costs, ensuring timestamping services remain accessible during unexpected events.
- Global Accessibility, Localized Costs - Electronic Timestamp as a Service provides global accessibility without maintaining timestamping infrastructure at multiple locations, resulting in cost savings associated with geographical expansion.
- Resource Utilization Efficiency - Cloud-based services enable efficient utilization of computing resources, ensuring infrastructure scales based on demand, preventing under utilization, and resulting in cost savings.
For further information, download Utimaco’s brochure on Electronic Timestamp as a Service.





