At the heart of secure online communications are SSL/TLS certificates and the certificate authorities (CAs) that issue them. These technologies not only encrypt our data but also validate the identities of the websites we trust with our sensitive information.
In this blog post, we will explore how SSL/TLS certificates and CAs work together to create a secure online environment, the historical evolution of web security, and the potential risks when this trust is compromised.
Trust origins – The history of secure web-based communication
Secured communication is one of the cornerstones of the web, enabling everything from e-commerce to banking and all other online services. In the early days of the internet, communication was based on HTTP, a protocol that transmitted data unencrypted. This meant that anyone who intercepted the communication between a user and a website—whether it be an internet service provider injecting advertisements or an attacker accessing passwords and private messages in a public WiFi—could see and modify all the information being transferred.
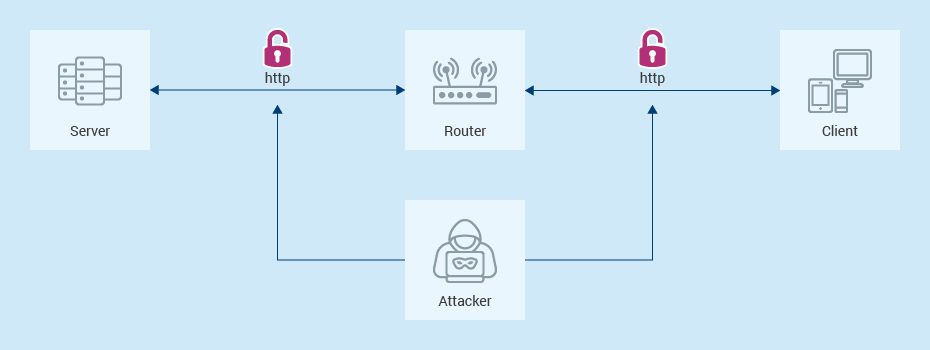
However, the introduction and standardization of HTTPS in 1994 and 2000, respectively, revolutionized online security. HTTPS leveraged cryptographic key exchanges when a user first connected to a server. Instead of transmitting information as plaintext, the keys generated during the exchange could encrypt both requests and responses, significantly limiting unauthorized access to private information. Without the decryption key, attackers could no longer read or alter the encrypted data – at least in theory.
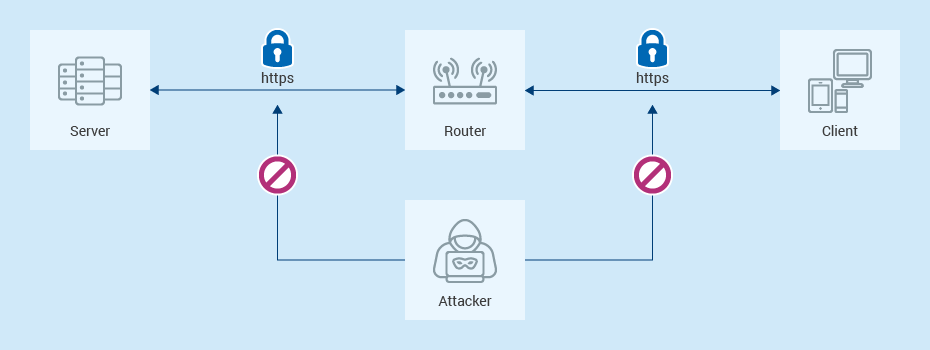
However, the security of this system hinges on trust and this lead us to key question:
How can I trust all actors involved in the key exchange?
For encrypted communications to be secure from third parties, users must be certain that the keys they are using when communicating with a website are legitimate. This is where TLS (Transport Layer Security) certificates and Certificate Authorities come into play. CAs authenticate that a specific TLS certificate belongs to the Website it claims to belong to. Without this authentication step attackers could simply trick users into using attacker-owned certificates, and the very foundation of online security would be at risk.
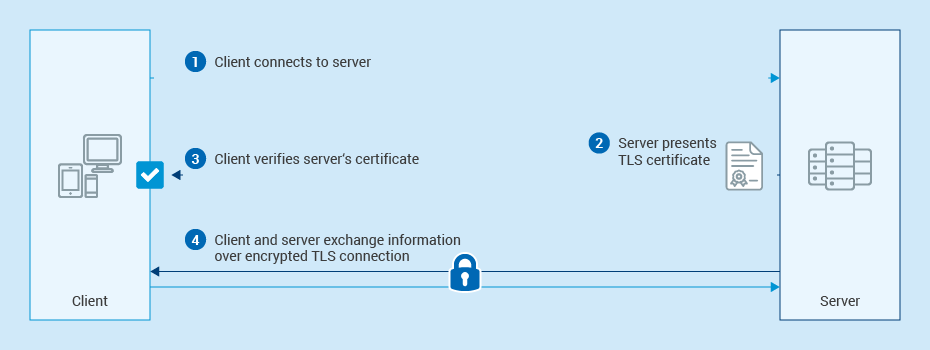
Establishing Trust: The Role of Certificate Authorities
Certificate authorities are essential to the security of online communications. They validate the identities of entities—such as websites, and less commonly email addresses, companies, or individuals—and bind them to cryptographic keys through digital certificates. This process ensures that users can trust the identities of the entities they interact with online.
A certificate authority performs several critical functions:
- Authentication: Validates the identity to which the certificate is issued
- Key storage: Make sure that no unauthorised parties can access or use the CAs keys to sign malicious certificates
- Certificate revocation, so that the impact of compromised certificates can be minimised
The issued digital certificates allow secure, encrypted communication between parties through public key cryptography. The CA verifies the identity of the certificate applicant and issues a certificate containing their public key, which is digitally signed by the CA's own private key, establishing trust in the certificate's validity.
In summary, certificate authorities ensure that users do not need to blindly trust the claims of a TLS certificate. Instead, they can trust and verify the signature of the CA, which has a proven track record of only signing legitimate certificates. This system underpins the security and trustworthiness of the internet.
The Risks of Untrustworthy Certificate Authorities
Trusted CA entities undergo strict audits, processes, and requirements to ensure their legitimacy and reliability.
But what happens if a certificate authority does not pass an audit and becomes untrustworthy?*
In short, this opens the door for attackers to impersonate any website, reading and modifying content sent to and from the user at will. This includes passwords, cookies, banking statements, and virtually any other sensitive information. Because a certificate authority can attest that a certificate belongs to nearly any web server, an attacker who controls or can manipulate a CA due to its lack of rigor can obtain a certificate for a victim website, including banks, shops, or government websites.
While such attacks are not always completely hidden, detecting them requires deep technical knowledge. Many of the fundamental assumptions about the security of the web rely on the trustworthiness of certificate authorities. If a CA becomes compromised, the entire chain of trust can be undermined, leading to potentially devastating consequences for online security and privacy.
*Just recently, Google has announced that they will no longer trust TLS certificates issued by the Entrust Certificate Authority (CA) starting November 1, 2024. Vist this blog post to read about key lessons to learn from this incident.
The role of Hardware Security Modules
Hardware Security Modules (HSMs) play a crucial role in Certificate Authorities by providing a secure environment for cryptographic operations and the private keys: HSMs generate and securely store the root and subordinate CA cryptographic keys. These keys are fundamental to the entire Public Key Infrastructure (PKI) and must be protected with the highest level of security. HSMs provide a tamper-resistant and tamper-evident environment for key storage, ensuring that the keys remain safe from unauthorized access or manipulation
Utimaco’s HSMs are designed to enhance the security of your cryptographic operations. Our u.trust General Purpose HSM Se-Series offers:
- Superior performance with up to 40,000 RSA 2K operations / s
- Multi-tenancy with up to 31 containers
- Crypto agility and PQC readiness
- FIPS 140-2 Level 3 certification (FIPS 140-3 in progress)
- Software Development Kit for custom implementations
Try for free with the fully functional simulator – ready for download from our portal
Lena Backes es una experta en marketing de TI con más de 10 años de experiencia trabajando en el sector B2B. En su carrera profesional, ha adquirido amplios conocimientos en diversas áreas, como la ciberseguridad, la gestión de redes, el streaming empresarial y la gestión de activos de software. En su puesto actual es responsable del posicionamiento de los productos y soluciones de ciberseguridad de Utimaco, con especial atención a la protección de datos, la tecnología Blockchain y la criptografía post cuántica.




