All areas of life are either or about to enter an accelerated process of digital transformation. In financial services, government, health, automotive, consumer facing processes and applications are increasingly becoming digitally implemented. The emerging internet of things, intelligent algorithms, big data and universal connectivity are accelerating the advent of ubiquitous digital services. Cashless payments become the norm rather than the exception, mobility becomes integrated and autonomous.
With the transparency and comparability of offers, non-existent transfer costs, customers become more demanding in their quest for an enhanced and customer-centric user experience.
As enterprises defend their market position in increasingly competitive environments and shrinking margins, companies evolve into service-integrating platforms, digitally supplying offers of meshed services, available across corporate boundaries and spread across a hybrid cloud.
What started in the telecommunication sector in the 1990s has reached security-sensitive sectors like financial services and government, as well as safety-oriented industries such as automotive, aviation and manufacturing, where platform-oriented value nets dynamically create new service compositions.
Security Processes Gain Relevance Across Industries
The quantity of simultaneously performed security-relevant digital processes requires high performance (e.g., in high frequency transaction processing), identity and access management (IAM) for securing the hybrid multi-cloud enterprise, data handling or bulk invoicing.
Digital transformation creates open flanks for cybercriminals. Security breaches have increased by 67% since 2014. By the end of 2021, the expected annual damage through cybercrime is estimated to reach $ 6 trillion (source: CyberObserver).
Gartner expects the worldwide spending on cybersecurity to reach $ 133.7 billion by 2022 (Gartner).
Variety and Agility in the Root of Trust
The Root of Trust to financial services or enterprise-grade security processes are Hardware Security Modules (HSM), generating, safeguarding and managing cryptographic keys to perform encryption and decryption functions.
Typical HSM-related use cases are transaction & payment processing, code signing, identity & access management, public key infrastructures, digital signature creation, blockchains, or time stamping.
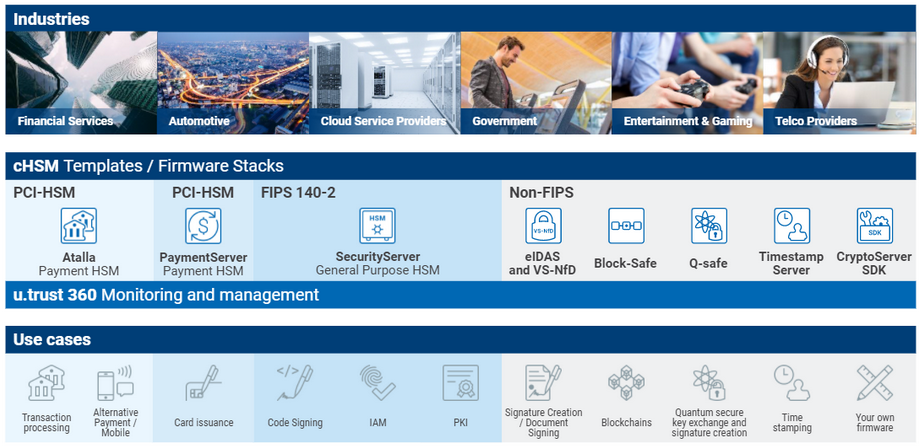
HSM technology has been developed to meet compliance standards that would be dependent upon the market and field of application. For example, payment servers require compliance to the Payment Card Industry standard PCI-HSM. Security processes like PKI require compliance to the FIPS-140-2/-3 standard, digital signatures need HSMs compliant to the eIDAS regulation, etc.
The composition of standards and regulated cryptographic algorithms may not remain the same over the life-time of the security architecture. Algorithms are becoming insecure over time as research and computing power progress, as well as cybercriminal inventiveness. This will lead to a continuous need for replacement. A noted example is the 3DES-algorithm, which was officially being retired by NIST on July 19, 2018. In view of the advancing quantum computers and the ephemerality of “safe” algorithms, the American National Institute of Standards and Technology NIST even suggests “candidate algorithms” until it will be safe to speak of a standard. Therefore, security infrastructure will require a high level of crypto-agility to be able to evolve with required standards and developing security requirements.
Converging and Simplifying the Root of Trust
In a study of 50 major data breaches, conducted by Boston Consulting Group, 72% of the failures were the result of “ an organizational failure, a process failure, or employee negligence.”
No wonder, given the quantity, dynamics and decentralization of composite services.
A big challenge is the diversity and heterogeneity of related data security infrastructures, leading to high cost of ownership and susceptibility to errors.
HSMs need to be able to protect data across the hybrid cloud, from the local datacenter to a third party cloud. It is vital that the operating company – the ‘data controller’ (regardless of whether it is a financial institution or an automotive manufacturer) maintains ownership of the keys, to avoid a vendor lock-in with a cloud operator but also to prevent access to unencrypted data by third parties.
Given the many different applications and regulations that require a level of compliance; HSMs are an important cost factor, as often many of these modules are needed to satisfy multiple requirements.
The increasing need for HSMs and the tendency towards service based infrastructures requires a cloud-agnostic HSM solution, able to seamlessly bridge the gap between on-premise and cloud deployments.
The first cloud HSMs which were available in the market since 2017 were able to configure policies per tenant however, they still were not able to satisfy the requirement for individual firmware, which forced users to deploy different hardware for different certification requirements.

This is where Utimaco delivered a disruptive innovation in 2021 – a fully containerized cloud HSM. With individual firmwares per container, Utimaco’s u.trust Anchor provides FIPS and PCI compliance in one platform, and satisfies requirements like non-repudiable digital signing or the useof quantum-safe algorithms (candidates).
Hardware consolidation is essential in order to eliminate the requirement for multiple devices. In turn, processes would be streamlined and workloads reduced, resulting in a minimised risk of human error. The total cost of ownership is minimized on two axes. Firstly, commissioning and maintenance effort is reduced. Secondly, the number of HSMs decreases. In fact the u.trust Anchor hosts up to 32 containerized HSMs in one module and efficiency of 40,000tps.
Considering the rapid transformative shift in security-relevant industries such as the financial services and automotive sectors, the u.trust Anchor platform is clearly best-in-class – it is the right product at the right time.







