Data shared with numerous stakeholders, both within and outside the organization, is a double-edged sword. While it fuels organizational growth, it also provides cybercriminals with opportunities to exploit for monetary gain or to tarnish an organization's reputation.
An effective way to ensure a seamless and secure data flow is through encryption, which transforms readable information into an unreadable format. However, this process should not alter your daily operations. Instead, it should help you maintain a secure data exchange. But first, let’s start with the basics.
Try our cloud-based version with the 30-day free trial
What is Data Encryption?
Data encryption is the process of converting data into a code (non-readable format) using an encryption key to prevent unauthorized access and boost data security. Only those with the decryption key can decode and read the data. This ensures that if data is intercepted or accessed by unauthorized parties, it remains protected.
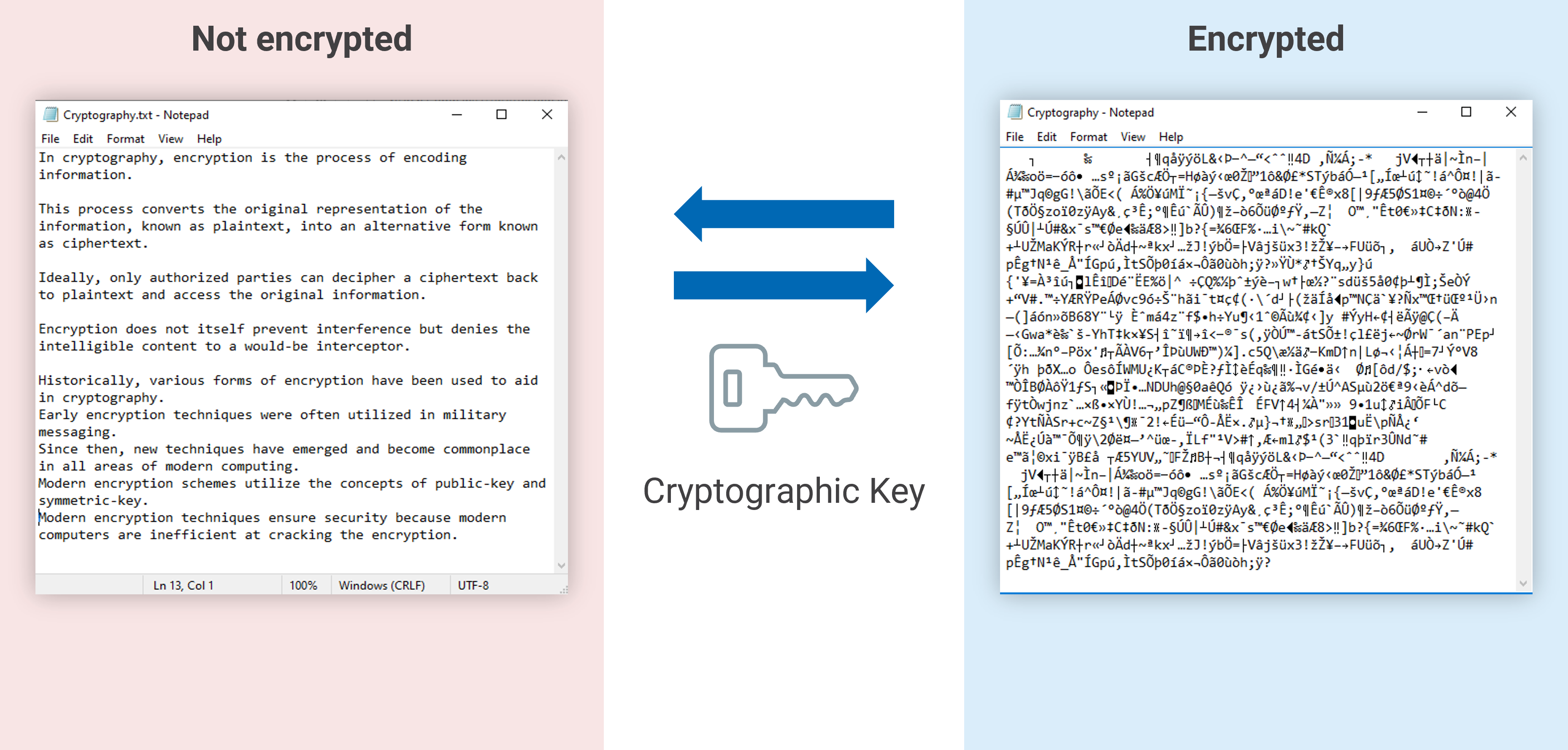
Why is Encryption Necessary?
With the escalating volume of sensitive data handled by organizations, the need for encryption (more precisely, file and folder encryption) is not just a trend but a necessity. Think about your own experience: how many documents do you handle on a daily basis to share information?
With data breaches becoming more frequent and sophisticated, the urgency of protecting confidential information—ranging from personal identification details to corporate intellectual property—has become paramount. Encryption ensures the data remains unreadable and secure even if unauthorized access occurs, mitigating data theft, financial loss, and reputational damage.
There is more…
Encryption not only safeguards data from unauthorized access but also ensures compliance with global regulations. It's a powerful tool that helps organizations meet their regulatory obligations while protecting sensitive information.
Overview of Data Protection Regulations
Almost all countries and industries worldwide have specific regulations in place to protect data. These regulations ensure security for various aspects such as intellectual property, financial records, health records, customer information, remote workforce, email and communication, data backup and recovery, and many more.
When examining regulations and their mandates on encryption solutions for various aspects mentioned above, it is clear that these standards are designed to enforce strict data protection policies across all sectors. These measures are also essential because human errors, even minor ones, can lead to significant losses.
Key Regulations Mandating Encryption
Regulations such as the General Data Protection Regulation (GDPR) in Europe, the Health Insurance Portability and Accountability Act (HIPAA) in the United States, and others globally all emphasize the necessity of encryption to safeguard sensitive information. These regulations require organizations to implement robust encryption protocols to ensure data privacy and security, whether data is in transit or at rest.
For example, GDPR mandates encryption as a critical measure to protect personal data and mitigate data breach risks, while HIPAA outlines specific encryption standards for healthcare information to prevent unauthorized access. Compliance with these regulations not only protects organizations from legal repercussions but also enhances your customer’s trust by demonstrating a commitment to data security. Thus, understanding and adhering to these encryption mandates is crucial for any organization handling sensitive information.
Below, you’ll find examples of a few regulations:
European Union
- GDPR mandates encryption to protect personal data.
- NIS2 boosts the use of encryption by essential entities to protect critical networks and information systems.
- With DORA, entities must use encryption to protect transaction data, customer information, etc.
Germany
- VS-NfD is for sensitive government information protection.
- TISAX is used to handle sensitive information in the automotive industry.
- KHZG mandates healthcare institutions to adopt encryption patient data protection.
USA
- CCPA requires businesses to implement encryption to protect consumers' personal information.
- HIPAA mandates encrypting electronic protected health information (ePHI) to secure patient data.
- Executive Order on Improving the Nation's Cybersecurity mandates the adoption of encryption to secure communications, data storage, and system access in federal government networks.
Asia
- The Philippines Data Privacy Act of 2012 mandates encrypting databases containing personal information and securing data in transit.
- PDPA in Singapore mandates encryption to protect personal data collected by organizations.
Universal Importance of Encryption
Looking at the regulations mentioned above, we can confirm that data encryption is a fundamental part of data protection for all use cases across all industries. Data Encryption ensures:
Integrity: Data is safeguarded against alteration,
Confidentiality: Only authorized parties can access data,
Availability: Authorized users can reliably access data whenever necessary.
Implementing Encryption: Where to Start
Data encryption is a critical component of modern data security strategies. By understanding and implementing encryption by global regulations, our organizations can protect sensitive information, comply with legal requirements, and build trust in an increasingly digital world. Whether dealing with healthcare data under HIPAA, personal information under GDPR, or government secrets under VS-NfD, encryption remains an essential tool in the fight against cyber threats.
Utimaco’s LAN Crypt File and Folder Encryption offers a software-based data encryption solution for securing your data. Transparency in encrypting all data according to policy guidelines protects against unauthorized access.
Try our cloud-based version with the 30-day free trial
Before you go, consider this: What are the key benefits of implementing data encryption for your organization beyond regulatory compliance? Reflect on this and explore how it could further enhance your business strategies.






