Key Escrow sounds like a relatively simple concept. Fundamentally, a Key Escrow is a secure storage of cryptographic keys and/or keying materials, enabling the true owner of the material to recover from loss. Perhaps an appropriate analogy would be to consider that a Key Escrow is like an Insurance Policy. Yet, a Key Escrow will not pay for your losses. Instead, a Key Escrow will ensure the data you have lost, will be recoverable. Unlike an emergency cash reserve hidden under the mattress, a cryptographic Key Escrow must be established and handled properly in order to remain effective.
To truly understand Key Escrow, its critical to understand how and where cryptographic keys should exist. From there it becomes even more crucial to understand the implications of each phase of the key management lifecycle.
How Should Cryptographic Keys Exist
To summarize numerous published industry standards, cryptographic keys should only exist in any one of three different formats.
1. Cryptographic Keys may exist in a certified hardware security module. This hardware security module must respond to any tampering event by making the cryptographic keys immediately unavailable. The most commonly accepted certifications are as follow:
- PCI PTS HSM
- FIPS 140-2 Level 3 or higher (recently replaced by FIPS 140-3 level 3 or higher)
2. Cryptographic Keys may exist in parts such that the full clear key or key pair are never made visible to a single individual.
- Symmetric Keys (e.g., TDES & AES) must be broken into two or more component parts.
- Asymmetric Keys (e.g., RSA & ECC) must protect the private key securely, while remaining free to share the unencrypted public key.
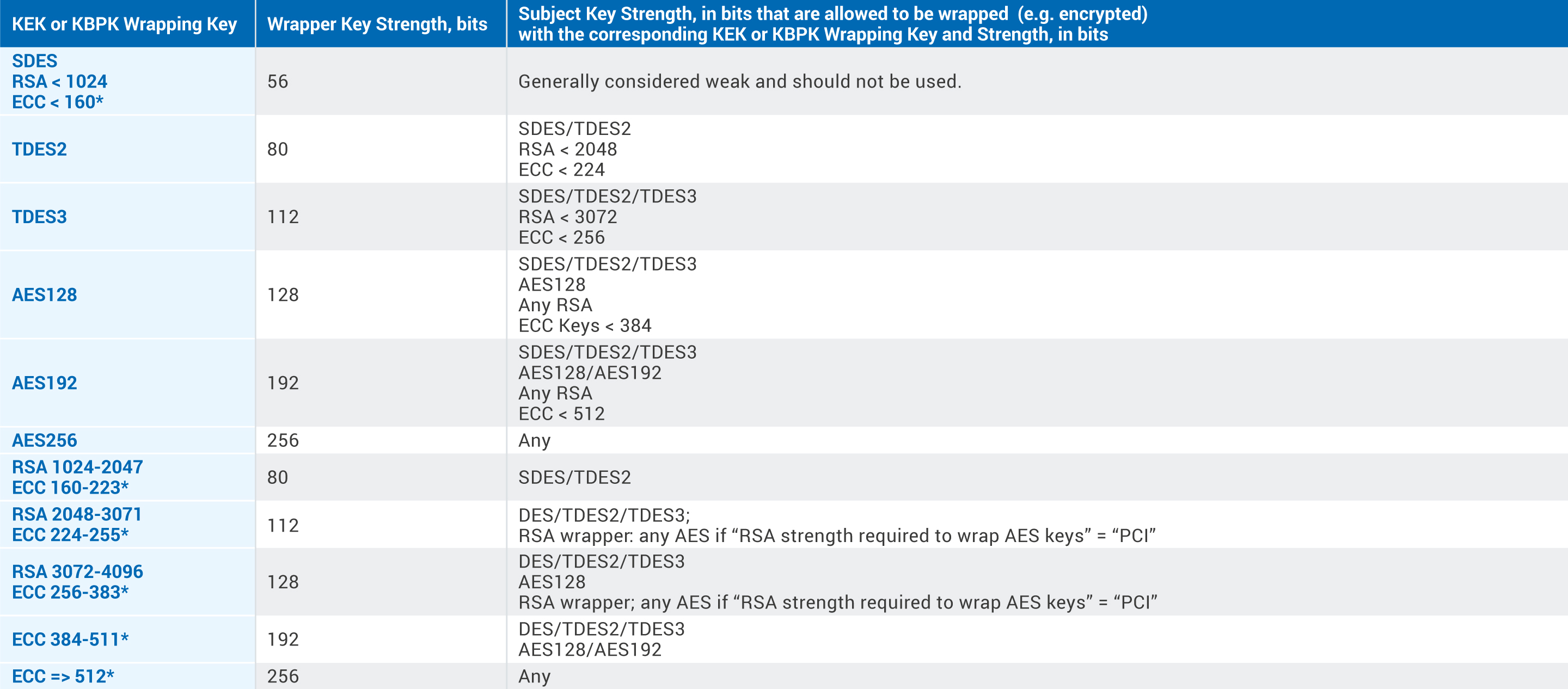
3. Cryptographic Keys may exist as encrypted by another cryptographic key of equal or greater strength. The chart below offers additional guidance:
The Key Management Lifecycle
Now, in consideration of the formats that keys may exist, it’s important to consider the various phases of the key management lifecycle. Of utmost importance, it remains imperative that any cryptographic key remains protected in one of the three aforementioned formats during any phase of the key management lifecycle.
The diagram above, identifies all possible aspects of the key management lifecycle. As a single diagram, it appears that all of these functions occur in the same physical location. While most phases of the key management lifecycle can function in the same physical location, Key Escrow is the one phase that absolutely must function from an independent and separately secured physical location. After all, Key Escrow is a disaster recovery concept. A disaster recovery (DR) infrastructure would never be deployed at the same physical site as the primary infrastructure. The same holds true for Key Escrow.
1. Key Generation – All keys should be generated using a certified random number generator. Typically, this will be completed using a Hardware Security Module. This ensures that the key exists in one of the three acceptable formats.
2. Key Distribution – Once a key is generated inside a Hardware Security Module, it may need to be distributed to various end points for usage. If a key must be distributed, it should only be distributed in parts, or as encrypted by another key of equal or greater strength.
3. Key Storage – If a key is to be stored outside of a Hardware Security Module, it should be stored in parts or as encrypted by another key of equal or greater strength. Keys will commonly be stored for the following reasons:
- Usage – Keys should only be stored for usage in a protected format. This will necessitate sending the protected key and the protected data back to the Hardware Security Module for decryption to ensure that the key is never visible in the clear.
- Backup – Like any other system or application, it remains prudent to maintain local backup copies of cryptographic keys, as long as they remain protected.
- Escrow – The most notable distinction between Backup and Escrow is the physical geographic location along with the physical security measures deployed in order to isolate and secure the keys for potential future use. Additionally, Escrow is a legal term permitting and, in some cases, demanding secure backups be available for such purpose.
4. Rotation – Is the concept of enforcing a defined cryptoperiod. All Keys should have a defined start and end date. Keys should be rotated based on the frequency of use. NIST 800-57 offers additional guidance on key rotation recommendations.
5. Archival – Is the practice of maintaining a cryptographic key locally. Maintaining a copy of a cryptographic key after the effective cryptoperiod, but within the primary infrastructure enables similar attack vectors that are otherwise mitigated through Escrow.
6. Destruction – Is the removal of cryptographic keys in all formats and locations, ensuring that a cryptographic key is no longer available for use in any manner in any location.
The attack vector of a cryptographic key is exposed for every instance that exists beyond its initial creation. Thus, the more a key is used, the more attack vectors are created. The more attack vectors that are created will help to define the importance of Key Escrow. The more a key is used, the more dependent the organization becomes on the availability of the key. When a substantial dependency is identified, the need for Key Escrow becomes self-evident.
KEES™ Key Exchange & Escrow Services: What Is It?
As the manufacturer of KeyBRIDGE, GEOBRIDGE by Utimaco has been operating the KEES Service since 2015. The KEES™ Service is the result of many organizations recognizing the need for a centralized key management utility. With the advent of “the Cloud” more and more organizations are eliminating physical infrastructure and associated capital expenditures. Further, as discussed in (Encryption, Key Escrow and Cryptographic Key management in the Cloud) many organizations lack the appropriate staffing to handle keys properly. This phenomenon has only been exacerbated because of the worldwide pandemic. Assembling employees in confined locations or infrastructure locations that prohibit gatherings, has caused the KEES™ Service to become a business necessity to ensure business continuity.
KEES™ is KeyBRIDGE “As A Service.” As a worldwide leading manufacturer of cryptographic solutions, GEOBRIDGE by Utimaco employs personnel that are experts and highly focused on cryptography and key management on a daily basis.
KEES™ Key Exchange & Escrow Services: How Does It Work?
All users of the KEES™ Service are assigned to a Centralized Key Manager that will oversee a team of Key Custodians. The KEES™ Service will act as primary or secondary for client operations. All keys generated by the KEES™ Service, will be generated using the HSM embedded within the KeyBRIDGE appliance. The HSM is a unique device exclusively offered by Utimaco, offering a hybrid mode for both FIPS and PCI PTS certifications.
Key inventories are managed within unique relationships and cryptographically segregated by Master Keys to ensure that each inventory is unique to its intended user. Key inventory reports are available on demand to include granular details of the full key life cycle for each individual key managed under the service. Monthly audit logs are provided with cryptographic assurance for integrity to document all possible activity. The service is maintained through dedicated GEOBRIDGE by Utimaco infrastructure. If you would like more information on the Key Exchange and Escrow Service download the Geobridge by Utimaco Professional Service document or contact us.
Blog post by Jason Way




