Hardware-Sicherheitsmodul zur sicheren Schlüsselerzeugung und -speicherung für vielseitige Anwendungsfälle
Die u.trust General Purpose HSM Se-Serie kombiniert überragende Leistung mit Multi-Tenancy. Diese Hardware-Sicherheitsmodule (HSMs) decken ein breites Spektrum an Anwendungsfällen ab, von der Einstiegs- bis zur Hochleistungsebene, und sind zukunftssicher konzipiert. Alle Modelle sind mit Post-Quantum-Kryptografie ausgestattet und nach FIPS 140-2 Level 3 zertifiziert.
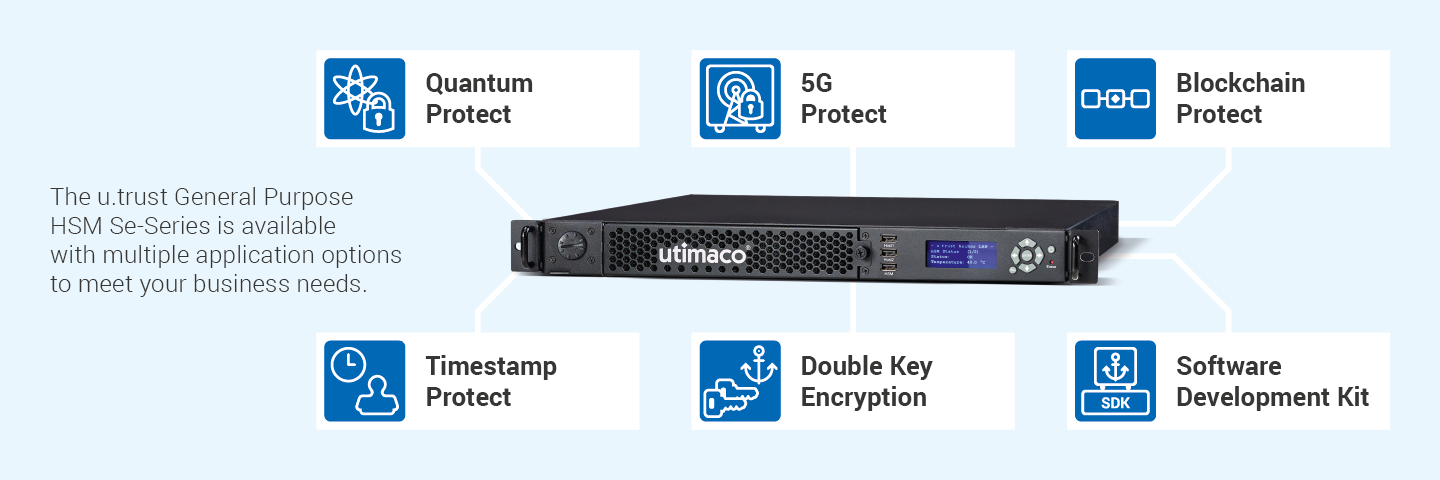
- Vielseitige Modelle vom Einstiegsmodell bis hin zu Hochleistungsanwendungen
- Vielfältige Anwendungsoptionen zur Erfüllung Ihrer geschäftlichen Anforderungen
- Überragende Leistung von bis zu 40.000 RSA 2K-Operationen pro Sekunde
- Mehrmandantenfähigkeit
- Krypto-Agilität und PQC-fähig
- Simulator enthalten
Produkttyp:
PlatformUnterstützte Firmwares:
Varianten
Vielseitige Modelle für Einsteiger- und Hochleistungsanwendungen
| Se100 | Se2k | Se5k | Se15k | Se40k |
| Bis zu 101 RSA 2K-Operationen / Sekunde | Bis zu 2.050 RSA 2K-Operationen/Sekunde | Bis zu 5.100 RSA 2K-Operationen / Sekunde | Bis zu 15.000 RSA 2K-Operationen / Sekunde | Bis zu 40.000 RSA 2K-Operationen / Sekunde |
| 1 Container | 4 Container | 8 Container | 4 Container | 12 Container |
Ihr Anwendungsfall erfordert mehr Container? Entdecken Sie das u.trust Converged HSM CSAR mit Optionen für 16 oder 31 Container in einem HSM.
Details

Kryptographische Algorithmen
- RSA, DSA, ECDSA mit NIST- und Brainpool-Kurven, EdDSA
- DH, ECDH mit NIST-, Brainpool- und Montgomery-Kurven
- Edwards-Kurven Ed25519 und Ed448
- AES, Dreifach-DES, DES
- MAC, CMAC, HMAC
- SHA-1, SHA-2, SHA-3, RIPEMD
- Hash-basierter deterministischer Zufallszahlengenerator (DRG.4 nach AIS 31)
- Echter Zufallszahlengenerator (PTG.2 nach AIS 31)
- Chinesische Algorithmen
- Alle Algorithmen sind im Produktpreis enthalten
Kryptografische Schnittstellen (APIs)
- PKCS #11
- Java Kryptographie-Erweiterung (JCE)
- Microsoft Crypto API (CSP), Cryptography Next Generation (CNG) und SQL
- Erweiterbares Key management (SQLEKM)
- OpenSSL
- Utimacos umfassendes Cryptographic eXtended Services Interface (CXI)
- Datenverschlüsselung
- Benutzer- und Geräteauthentifizierung
- Signieren von Dokumenten
- Blockchain-Prozesse
- Code-Signierung
- Teilnehmerauthentifizierung in mobilen Netzwerken
- Schlüsselvereinbarung in mobilen Netzwerken
- Ausstellung von Zertifikaten
- Infrastruktur für öffentliche Schlüssel
- Erstellung von Zeitstempeln
- Personalisierung von Chips und Geräten
- PQC-Anwendungen
- Und vieles mehr