The use of HSMs for the security of business applications has been mandatory since the last decade.
Driven by the intend to handle a large number of clients within an HSM, multi-tenant HSM architectures are getting popular as they promise robust performance, dedicated security configurations, easy and fast integration ensuring business continuity.
As business grew, so did the threat of compromise or theft of data. To address these risks, both software methods and hardware devices were produced to secure networks, systems and data. HSMs are dedicated devices, incorporated with both logical and physical protection mechanisms, designed to provide separate, secure operating environments where confidential or sensitive information could be treated without risk of exposure.
The benefits of an HSM include strong protection of the life-cycle of cryptographic keys, accelerated cryptographic operations, multi-factor, and ‘four-eyes’ authentication, and resistance to side-channel attacks that rely on logical or direct access to the hardware. Using an HSM for protection against the risks of compromise or theft of data, results in a higher security and performance efficiency
1. Multi-tenancy and HSMs
HSMs are critical security components for the security of data and business applications. In certain industries and for specific use-cases, the use of an HSM is mandatory. And the case could be made, that where it isn’t – yet – mandatory, it is still best practice to use an HSM where an HSM can be used.
As they are dedicated hardware modules with high-speed cryptographic operations capability so a single HSM or an HSM cluster (managed by a single server application) is used by various services and applications via HSMaaS (HSM as a Service) model. The corporate level cloud-based and network-attached HSMs are used by a large number of clients/tenants and thus need to have the capability of allowing for multi-tenancy. In a forthcoming article we will discuss use cases where Multi-tenancy makes sense, from a technical or business point of view.
2. Advantages offered by multi-tenant HSM architectures
Multi-tenant HSM architectures can offer the following as advantages, but may also suffer from certain disadvantages:
- Dedicated Security Settings: Each tenant and its corresponding data are securely and independently managed as per its configurations, policies, and delegation of duties.
- State of the art Performance: HSM architectures with multi-tenancy support deploy and incorporate state of the art professional HSM devices and tenants can easily offload the complex calculations-based cryptographic operations to HSMs improving the overall system performance. They also incorporate hardware-embedded support for algorithms, caching, multi-threading and potentially performance optimization techniques to achieve the performance.
- Business Effectiveness: The HSMaaS architecture providers ensure HA (High Availability) and load balancing features, so the tenants enjoy accelerated performance along with smooth connectivity ensuring business continuity.
- Easy Integration and Management: Standard multi-tenant HSM architectures support fast application integration and deployment managed by a centralized management interface. The integration with business applications is enabled via common, standards’-based APIs supported on almost all OS and development platforms. Current implementations (first and second generation) of HSMaaS use single dedicated devices and fast switching -- ie, the HSM pool, or farm is multi-tenant, but each HSM is single-resident-at-a-time
- Less Deployment & Integration Costs: Even in your own data-center, HSM deployment incorporates logical protections but also physical protections such as locks, alarms, and security cameras etc. and manpower to manage all these things. Secure HSM architectures with multi-tenancy support can provide the same services and tenants don’t have to bear all the deployment costs.
- Intrusion Detection/Alerting & Audit Mechanisms: As a multi-tenant HSM architecture serves a large number of tenants so there are more chances of security breaches and threats. Multi-tenant HSM architectures must incorporate security controls for the detection of, and alerting mechanisms about intrusion and unauthorized access attempts, or misuse. The administrators of the architectures can view the access logs to verification.
- Standard and Legal Compliance: Clients always select the vendors which possess international certifications such as FIPS 140-2 (Level 3 or higher) and Common Criteria which enable the trust on sellers/vendors that the security devices are formally tested for security loopholes and vulnerabilities. Certified HSM architectures ensure secure and accelerated cryptographic operations along with regulatory/legal compliance.
3. Tasks to be accomplished by secure multi-tenant HSM architectures
The challenges faced by Multi-tenant HSM architectures can be enlisted as:
- Dedicated Data Security at Scale: Key management mechanisms of a large number of tenants are handled by a single multi-tenant HSM architecture. It’s a big challenge for these architectures to securely manage the keys, data and security policies of each tenant. Proper implementation of role-based policies for data accessibility is mandated. A big challenge is to implement the data protection approaches and mechanisms recommended by NIST and other standards.
- Proper Implementation of Authentication Mechanisms: Multi-tenant HSM architectures must incorporate strict and enforceable authentication mechanisms so that each tenant only gets the system-use-authorization after authentication.
White-listed or authorized access patterns should only be allowed access to the systems. - System Efficiency: Clients make use of multi-tenant HSM architectures to offload the time consuming and complex cryptographic operations and the management of keys or associated data. Tenants may include various banking and payment systems which can’t bear the delays and performance issues which result in business loss. Achieving acceptable performance while securely serving a large group of tenants is a big challenge for these systems.
- Threat Detection and Audit Management: As the multi-tenant HSM architectures are the cryptographic data custodians of all the tenants, there must exist advanced level logging, alerting and audit mechanisms. The patterns for authorized users access rights they need;- all the patterns for unauthorized access should not be granted access and attempts should be logged properly for further analysis. A further way forward for this approach is to provide integration with well-known SEIM solutions such as QRadar and ArcSight etc.
- Affordable Cost: For multi-tenant HSM architectures, the ownership cost (procurement, deployment, and management) cost is borne by the service provider. Tenants just pay the usage charges and enjoy the benefits of corporate level HSMaaS services. There should be a balance between the price charged by the HSMaaS providers and the feature set offered to compete in the business market.
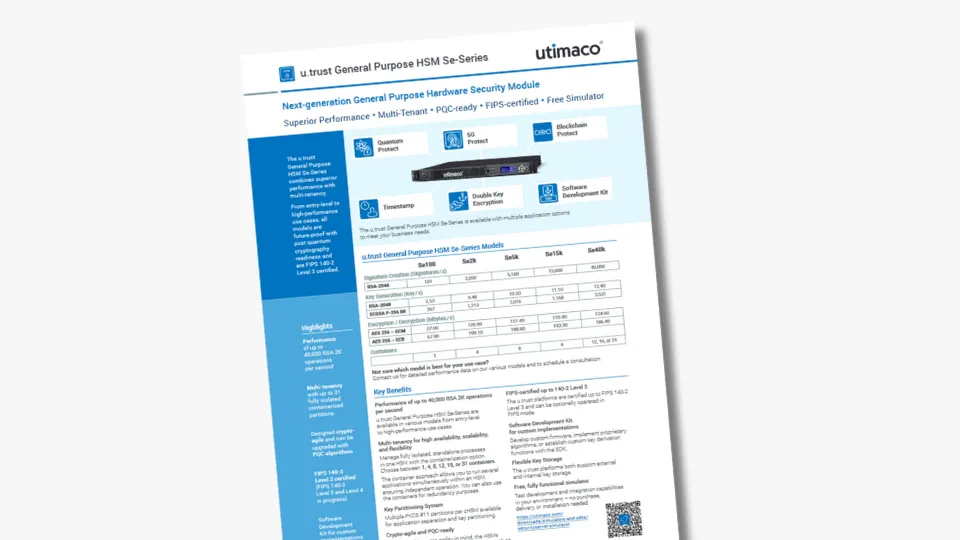
Experience true multi-tenancy within a single Hardware Security Module
Utimaco's u.trust General Purpose HSM Se-Series and u.trust Converged HSM CSAR both offer models with multiple containers (up to 31). This cloud-inspired, container-based approach allows organizations to run fully isolated, independent processes in each container. The containers are therefore referred to as cHSMs (containerized HSMs). In addition, each cHSM provides multiple PKCS #11 partitions for further application separation and key partitioning. This makes the HSMs ideal for all types of cryptographic applications, as they can be upgraded with different application option packs to address specific use cases such as blockchain and 5G mobile networks.
With the container option, the different applications can run simultaneously, but independently of each other. This is ideal for organizations that need to run cryptographic applications for different customers or for highly regulated use cases.
In addition, its flexibility extends to customization, allowing the implementation of proprietary algorithms and the creation of customer key derivations using the software development kit.
Conclusion
The use of HSMs for the security of business applications has been mandatory in payment related applications for many decades. As the number and the cost of breaches is on the rise, many CISOs are reconsidering their security architectures – to include the use of HSMs. Consequently multi-tenant HSM architectures are getting popular but still come with a number of drawbacks and security risks.
If you are interested in finding out how Utimaco will solve the challenges and limitations that are part and parcel of the multi-tenant cloud in the market today – get in touch.