Protecting People, Data, and Infrastructure – Today and Tomorrow
Utimaco has been committed to protecting people and securing critical infrastructure with trusted, adaptable cybersecurity and compliance solutions. With a strong legacy in securing data, transactions, and identities, we empower businesses and governments worldwide to navigate an increasingly digital and connected world with confidence.
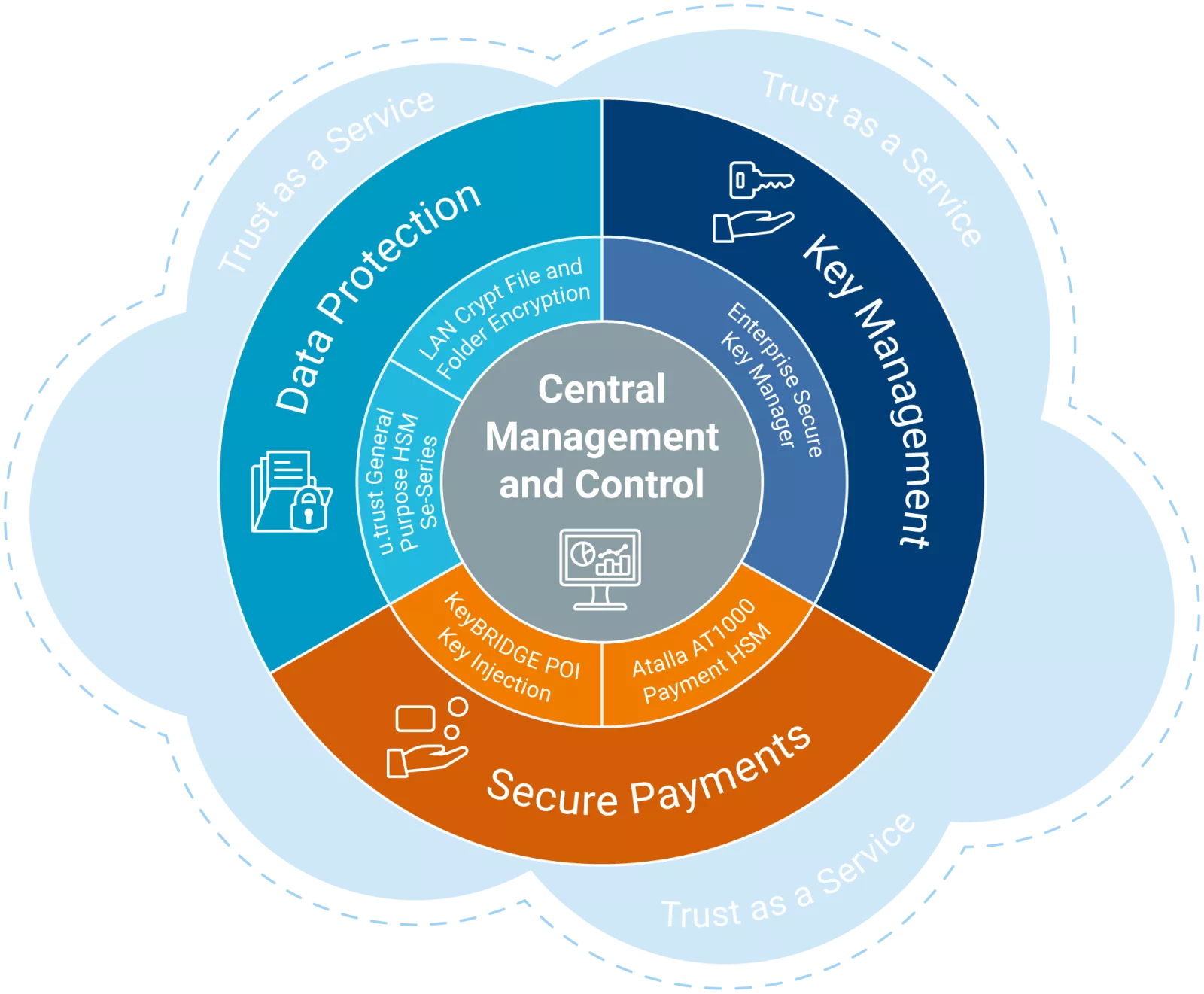
Strong & Reliable Cybersecurity - Protecting What Matters
Utimaco’s Information Security division delivers robust cybersecurity solutions built on innovation and technical expertise - because cryptography is in our DNA.
We protect:
- People, devices, and digital identities against cybercrime
- Financial transactions, data at rest and in motion against theft and sabotage
- The digital economy and digital transformation processes against theft, misuse and manipulation
Our proven, future-proof technology, products, and solutions meet the highest regulation and compliance standards for data protection, key management and secure payments – on premise and as a service.
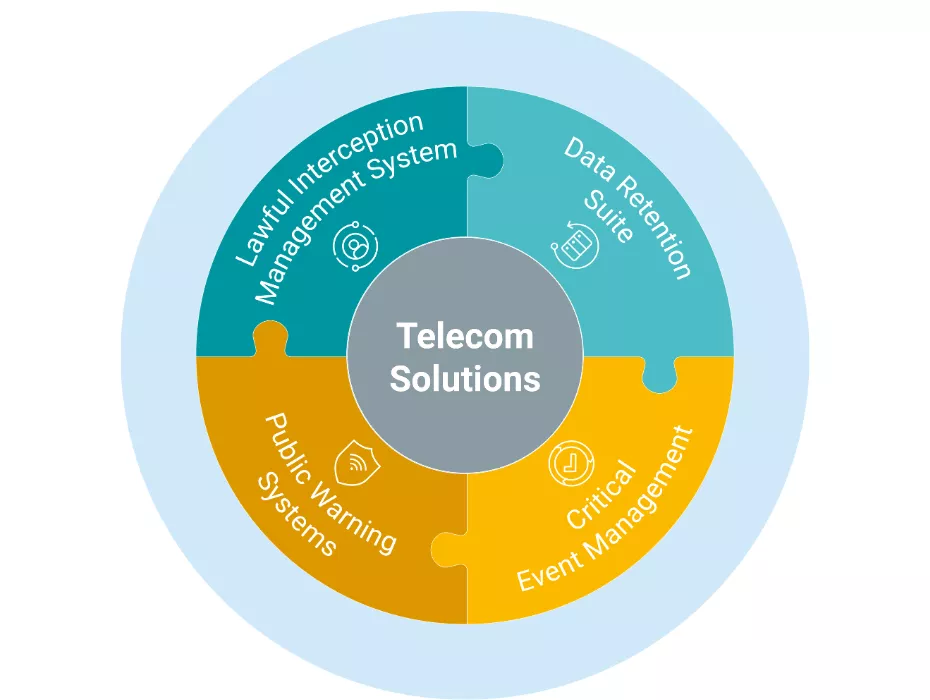
Telecom Compliance and Public Warning Solutions
Utimaco’s Telecom Solutions division offers compliance solutions and public warning systems.
Utimaco’s carrier-grade systems enable real-time monitoring and long-term data retention in public telecommunication networks since 1994. Utimaco is the preferred partner of many of the world’s leading network equipment vendors. With around 300 installations in over 90 countries, Utimaco is one of the leading global suppliers in the Lawful Interception and Data Retention market. Being also the world’s largest CBC (Cell Broadcast Center) provider, the company has deployed its warning solutions across more than 400 MNOs and tens of governments across the globe.