UTIMACO - securing the broadband network for Lawful Interception of broadband data traffic
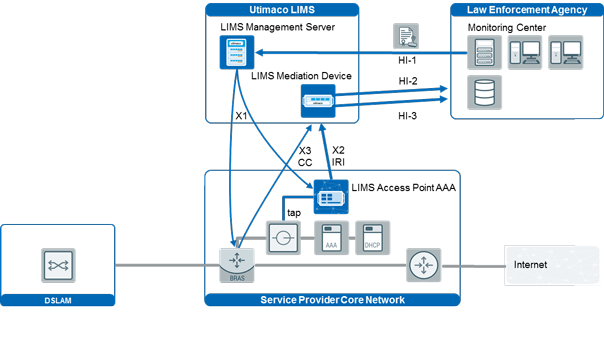
When it comes to intercepting communications between parties of interest to Law Enforcement agencies via internet access networks, there are generally two options: active and passive interception methods;
With active interception, available network nodes, such as routers and Authentication, Authorization, and Accounting (AAA) servers, provide capabilities to monitor the authentication data as well as the IP media stream of persons under surveillance. Passive methods, on the other hand, rely on non-intrusive network probes that monitor all traffic and are integrated into the operator’s network. In some cases, combining active and passive methods ensures optimal results or is the only viable option.
Utimaco LIMS supports a large range of network routers and access gateways for virtually any type of broadband network. LIMS implements many vendor-specific interception methods, such as Cisco SII, Juniper DTCP, Nokia LIP, and many others.





