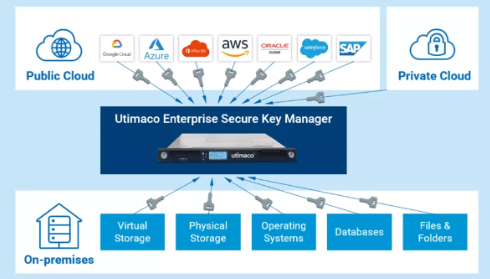
Enterprise Secure Key Manager enables individual key management strategies by providing a single pane of glass for all cryptographic keys, whether on-premises or in the cloud.
Due to its broad integration capabilities, it is acknowledged as trusted solution for a variety of technology partner integrations with companies around the globe, such as Dell, HPE or NetApp.
Enabled through its crypto-agility it is also capable to manage keys created with post quantum cryptography algorithms recommended by NIST and BSI.
*: for ESKM L3 and ESKM L4 (physical)
** FIPS 140-3 Level 2 appliance (pending), FIPS 140-2 L3 and L4 (embedded HSM)





















