Since the mid-1990's, there has been an awareness that public-key systems could be compromised by quantum computers. This has resulted in a critical requirement to protect systems from future deployment of cryptanalytically relevant quantum computers (CRQC).
Over the years there has been significant progress in research conducted by various industries, academics and governments that concludes that quantum computing will someday come to fruition. This research provides further credible proof that now is the time to prepare for effectively transitioning to quantum-resistant (QR) algorithms, which includes such things as planning and budgeting. By doing so, National Security Systems (NSS) and related assets can be assured continuous protection once cryptanalytically relevant quantum computers do arrive.
What is the Commercial National Security Algorithm (CNSA) Suite 2.0 and what does it apply to?
A recent cybersecurity advisory from the United States National Security Agency (NSA) notified NSS operators, owners and vendors of what the future requirements for quantum-resistant algorithms will be for NSS. These post-quantum algorithms have been thoroughly tested and analyzed to assure they are secure against attacks from quantum computers and computer technology that is currently in use.
NSA’s Commercial National Security Algorithm Suite 2.0 serves as an update to the current algorithms in CNSA 1.0. When further updates to algorithms are required, the version number will be modified.
The algorithms provided in the Commercial National Security Algorithm Suite apply to all NSS use of public cryptographic algorithms. This includes all used on NSS, whether classified or unclassified. The use of any other cryptographic algorithms that are not approved by the National Manager are typically forbidden unless a waiver has been obtained.
In this review of NSA’s Commercial National Security Algorithm Suite 2.0, we will focus on the following areas:
- Algorithms for Software and Firmware Signing
- Symmetric Key Algorithms
- General Use Quantum-Resistant Public Key Algorithms
- General Timing and Transition Method
Algorithms for Software and Firmware Signing
NSA recommends the following algorithms for software and firmware signing:
- Leighton-Micali with SHA-256/192 (LMS)
- Xtended Merkle Signature Scheme (XMSS)
For some time, The National Institute of Standards and Technology (NIST) has standardized algorithms for software and firmware signing. However, this changed with the release of the Commercial National Security Algorithm 2.0, and now NSA is using these algorithms for this specific use case.
There are three reasons why CNSA 2.0 algorithms are to be used for software and firmware signing:
1. These algorithms have already been standardized by NIST. Other post-quantum signature algorithms have not been standardized as of yet.
2. There is an urgent need for this signature use-case.
3. This usage helps keep track of how many times a specific public key is used in signing software or firmware.
Symmetric Key Algorithms
The requirements for symmetric key algorithms have only changed slightly from CNSA 1.0 to CNSA 2.0. Advanced Encryption Standard (AES) as specified under FIPS Pub 197 which uses 256-bit keys for all classification levels remains as a symmetric-key algorithm. With CNSA 2.0, Secure Hash Algorithm (SHA) 384 or 512 as specified under FIPS Pub 180-4, is approved for all classification levels.
General-Use Quantum-Resistant Public Key Algorithms
Commercial National Security Algorithm Suite 2.0s general-use quantum-resistant public key algorithms are the main public-key algorithms used by most applications. Currently, these algorithms have been selected by and recommended by NIST for standardization for post-quantum cryptography. As of yet, neither FIPS-validated implementations nor final standards are available. The NSA has announced the selection of these future NSS requirements to allow vendors to prepare for the required implementation of these standards.
The CNSA 2.0 quantum-resistant public-key algorithms will be:
- CRYSTALS-Kyber as asymmetric algorithm for key establishment
- CRYSTALS-Dilithium as asymmetric algorithm for digital signatures
General Timing and Transition Method
The transition timing for NSA’s Commercial National Security Algorithm Suite 2.0 will depend upon the proliferation of standards-based implementations. The NSA is aware that different technologies will have different paces for adopting QR algorithms. It expects that the NSS transition to QR algorithms should be complete by 2035. When configuring systems during the transition period, NSS owners and operators are required to prefer CNSA 2.0 algorithms where feasible.
Source: Commercial National Security Algorithm Suite 2.0
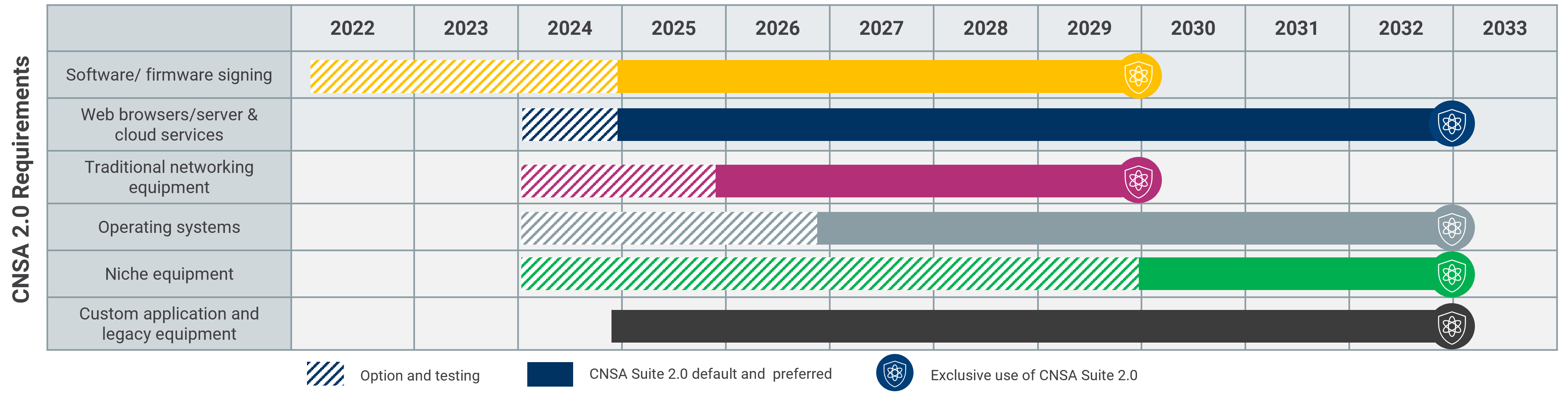
The NSA recommends that the transition for software and firmware signing begins immediately in addition to:
- CNSA 2.0 signing algorithms will be used by 2025 for new software and firmware.
- Deployed software and firmware that is not CNSA 1.0 compliant be transitioned to CNSA 2.0 compliant algorithms by 2025.
- All deployed software and firmware transitioned to CNSA 2.0 signatures by 2030.
Additional requirements for implementing other CNSA 2.0 requirements for NSS, include:
- Begin transitioning immediately for software and firmware to CNSA 2.0 by 2025 and by 2030, exclusively use CNSA 2.0.
- Support and prefer CNSA 2.0 by 2025 for cloud services and web browsers/servers by 2025 and only use CNSA 2.0 by 2033.
- Begin supporting and preferring CNSA 2.0 by 2026 for traditional networking equipment, such as VPNs or routers and exclusively use CNSA 2.0 by 2030.
- Support and prefer CNSA 2.0 by 2027 for operating systems and only use CNSA 2.0 by 2033.
- Large public-key infrastructure systems and other niche equipment should support and prefer CNSA 2.0 by 2030 and by 2033, only use CNSA 2.0.
- Update or replace non-compliant custom applications and legacy equipment by 2033.
In line with NSA’s recommendations, companies should immediately prepare for post-quantum technology and protect the future of their business. By identifying and evaluating vulnerabilities, this leads to a crypto infrastructure ‘compatibility’ with quantum-safe algorithms. Start by testing PQC algorithms in your environment!
Algorithm Suite: Recent Update
On April 2024, the NSA released updates and clarifications to the Algorithm Suite in the form of an FAQ document. The document clarifies terminology, explains the timeline, preparations and more.
There are three statements that we would specifically like to highlight:
- It is not enough to adjust the key sizes of RSA and ECC! The document clearly states that RSA and ECC will not be suitable to achieve quantum resistance.
- If you want to use LMS or XMSS for software or firmware validation, Hardware Security Modules (HSMs) are an important aspect. Signing and state management should be managed in hardware to ensure the security of the signatures. The design of the architecture and backup management must prevent state reuse.
Read more about state management for LMS and XMSS.
- The NSA reiterates the need to implement quantum-resistant algorithms today, such as AES-256, SHA-384, SHA-512, and the NIST hash-based signatures listed in NIST SP 800-208. For the other algorithms recommended by NIST and NSA that are not yet standardized, implementation efforts should also be made and problems reported.
References
Commercial National Security Algorithm Suite 2.0
The Commercial National Security Algorithm Suite 2.0 and Quantum Computing FAQ









