Due to the exponential increase in cyber threats and attacks, Zero Trust Architecture (ZTA) has become the latest trend in enterprise cybersecurity. ZTA is also referred to as perimeter less security. The working principle of this architecture is founded on not trusting any network element, even if they reside inside the network perimeter and maintaining strict access controls. This article highlights the need, working principles, and components of Zero Trust Architecture.
Why is there a Need for Zero Trust Architecture?
There is an ancient well-known proverb "Necessity is the mother of invention" which implies that when the need for something becomes imperative, you are forced to find ways of getting or achieving it. This digital transformation became critical to organizational sustainability and the proliferation of “work from home” policies. The assets in an IT Infrastructure include identities, devices/ endpoints, application/data, infrastructure, etc. having different criticality, value, and risk exposure. As a consequence, conventional perimeter security solutions proved inadequate to secure the assets, with an alarming increase in breaches rendering the concept of nonexistent trust. Trust is being viewed as a vulnerability.
What is Zero Trust Architecture?
Zero Trust is based on the theory “Never Trust, Always Verify” and necessitates stringent and constant identity verification to lessen implied trust zones. Zero trust assumes that no implicit trust is granted to an organization’s assets based solely on their physical/network location or asset ownership, along with Multi-Factor Authentication (MFA) and authorization mechanisms. A reference model/standard for Zero Trust was published by NIST “SP 800-27 Zero Trust Architecture” mandated to provide direction to build Zero Trust Architectures (ZTA). It is a very comprehensive standard that needs to be adhered to by government and private organizations along with providing vendor independence. It also ensures compatibility and protection against modern attacks for a ‘cloud-first, works from anywhere’ model that most enterprises would need to achieve.
Microsoft also provide a further example of ‘zero trust defined’, where every access request is fully authenticated, authorized, and encrypted before granting access.
Zero Trust Architecture design is based on the assumption that there is no conventional network edge and the networks can exist locally, in the cloud, or in a hybrid combination with resources, and users can exist anywhere. ZTA exhibits to be a detailed security framework mandating all the inside/outside users to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or maintaining access to data, and applications.
What are the Working Principles of Zero Trust Architecture?
The working principles of ZTA are as follows:
Trust None, Always Verify
It implies that a trusted identity, device, application, credential, or zone (i.e, a segment of the network) does not exist at any point in time. Therefore, verification and validation mechanisms should be applied each time a resource is being accessed by an entity.
Minimize Attack Impact
Another critical objective of Zero Trust Architecture is to reduce the potential impact of an attack. It can be achieved through the incorporation of end-to-end encryption, continuous monitoring, micro-segmentation (at the user/data/credential level), the principle of least privilege, and automated threat detection and response mechanisms. ZTA also limits the scope of credentials or access paths for an attacker, creating a time bracket/window for the response systems and people to thwart and neutralize the attack. Further mechanisms such as Just-in-time (JIT), Just-enough-access (JEA), and risk-based policies can further improve system security.
Effective Context Collection and Analysis
“The more we see, the more we can defend”. ZTA mandates generating the most effective and precise conclusion. There is a need to integrate behavioral data from the entire IT stack (identity, endpoint, workload, etc..) for the most accurate response. It can also be achieved through integrated extended detection and response (XDR) that provides end-to-end visibility, automates response to protect assets, remediate threats, and support investigations. Further systems that can assist in this regard are Continuous Diagnostics and Mitigation (CDM), Security Information and Event Management (SIEM), and Cyber Threat intelligence.
What are the Components of Zero Trust Architecture?
ZTA uses a control plane responsible for network control communication and a data plane that is used only for application/service communication flows.
The components of ZTA are as follows:
- Policy engine (PE): It is accountable for the conclusion to allow/disallow access to resources based on enterprise policy and input from external feed sources such as SIEM, CDM, and Threat Intelligence Systems. The PE is paired with the policy administrator component. The policy engine makes and logs the decision (as approved, or denied), and the policy administrator executes the decision.
- Policy administrator (PA): It is mandated to establish and/or disrupt the communication path between a subject and a resource. It generates session authentication tokens which are further used by the subject to access a resource. It works in collaboration with PE and depends on its decision to eventually allow or deny access.
- Policy enforcement point (PEP): This component is accountable to monitor, enable, and terminate connections between a resource and a subject. PEP interacts with PA to forward requests and/or receive policy updates from the PA. It is the logical component of ZTA and its implementation exists on the subject and gateway for the protection of resources.
The implementation of ZTA in an organization requires the input feed and policy updates from various internal and external components which are utilized by Policy Engine for the decision on access requests as follows:
- Data Access Policies: This component defines and maintains the rules, attributes, and policies about access to system resources. These rules may be dynamically generated by the policy engine or in encoded format. This component is the first consulting point by the Policy Engine for decision-making as it holds basic access privileges for accounts.
- Industry Compliance System: The compliance with standards and regulations not only makes the system secure but also increases the customer trust/confidence in the system. This component guarantees that the system remains compliant with the applicable standards and regulations.
- Threat Intelligence Feed: This component includes the feed from internal or external sources that is further input to the Policy Engine for making access decisions. It may include several services receiving data regarding recent vulnerabilities, attacks, software bugs, and malware signatures that feed the Policy Engine.
- Continuous Diagnostics and Mitigation (CDM) System: It performs the task of continuously monitoring the state of the system assets and provides a report to the Policy Engine which further applies updates to software and configuration components based on the report.
- ID Management System: This component is mandated to create, store, and manage identity records and system accounts by incorporating a Lightweight Directory Access Protocol (LDAP) Server.
- Network and System Activity Logs: This component collects the asset logs, resource access actions, and other events that provide real-time feedback on the security posture of enterprise information systems.
- Public Key Infrastructure (PKI): This component is mandated for the issuance of x.509 digital certificates to various system entities such as subjects, services, resources, and applications.
- Security Information and Event Management (SIEM) System: This component accumulates security-centric information for further analysis. SIEM data is also utilized to improve and enhance policies and warn about possible attacks against system assets.
What are the Core Challenges of a Zero Trust Architecture?
Identity Management
We pass through many examples of account phishing and takeover etc on a daily basis, due to the gaps in existing identity management solutions. ZTA suggests identity management roles with higher and lower privileges along with proper audit control so that a compromised identity must not harm the system.
Authentication
The implementation of typical perimeter security failed to provide enough protection. Once passed through the enterprise firewalls of organizations, hackers and malicious entities are considered to be authenticated, as there were minimal authentication mechanisms on the internal systems. ZTA mandates authentication via multiple factors such as username/password, location, OTP, digital certificate, security key, etc.
Access Management
The legacy access management model was “trust but verify”. When it comes to access management, Zero Trust Architecture redefines the model as “never trust, always verify, enforce least privilege” along with other factors such as who is requesting access, the context of the access request, and the corresponding risk. The implementation of an effective access management solution in ZTA requires extensive, HSM-secured identity management, with sophisticated zero trust policies and fine granular role management.
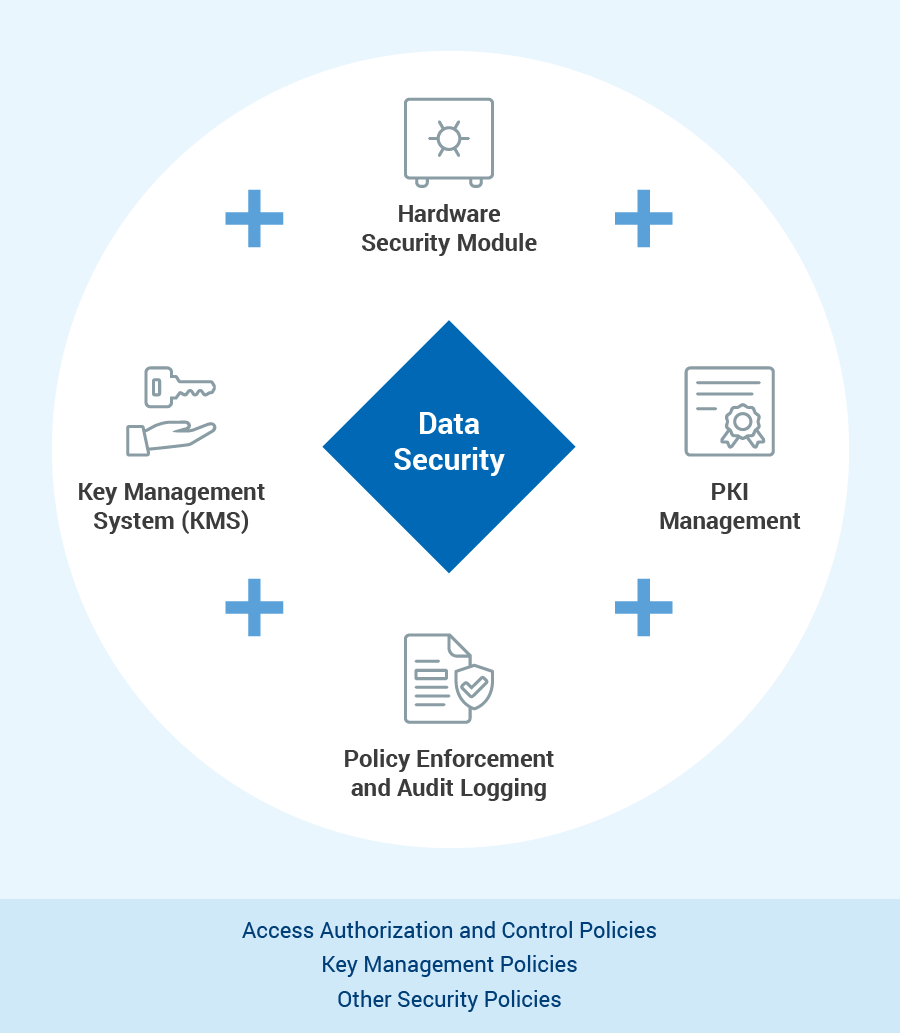
Data Protection
ZTA mandates the security of the complete lifecycle of data during transit, at rest, and in use. The mandatory component for the subject goal is the incorporation of not only a public key infrastructure but also key management system, and dedicated encryption software.
Zero-Trust Must Be End To End
To avoid any gaps, the complete corporate process must be implemented with zero-trust. Island solutions need to be replaced by a zero trust design that embraces proactive cybersecurity architecture and also reactive incident response processes.
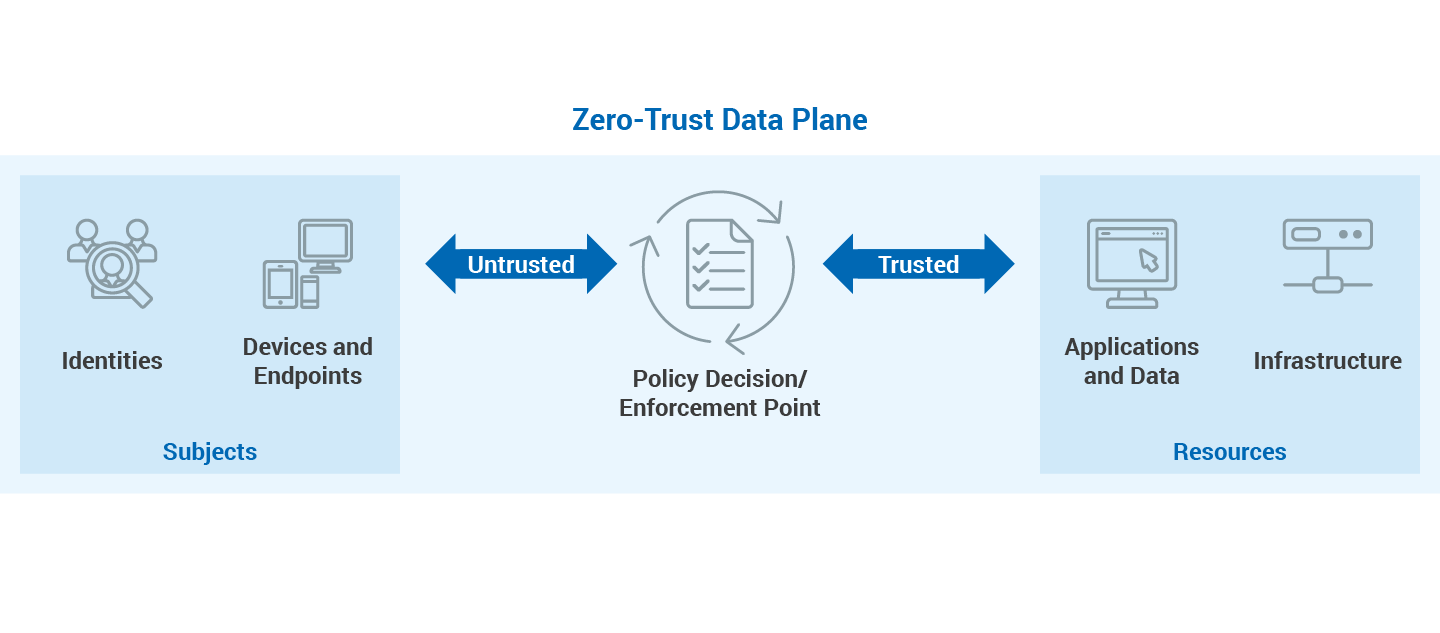
From a functional point of view, a zero-trust architecture needs to be based on:
- A central zero trust strategy that includes hardening technologies such as HSMs as a root of trust, as well as key management, policy management, policy enforcement, and audit logging
- Identity management, managing human identities, devices, and endpoints
- Authentication infrastructures for human identities, devices, and endpoints
- Access Management for users, devices, endpoints, and applications
- Data Encryption for applications, data and infrastructure
Utimaco's security solutions enable organizations to implement true Zero Trust Architectures.
Contact us to discover more and to help you achieve your digital transformation objectives.