In a data-driven world, one truth remains unwavering: security is paramount.
Whether it's protecting critical medical data or enhancing sensitive government information, the choice of hardware security modules (HSMs) is crucial. HSMs provide the highest level of security due to their specialized design and encryption capabilities. They offer robust protection through cryptographic key management and secure storage, ensuring that sensitive information remains inaccessible to unauthorized parties.
Utimaco stands out as the better choice among HSM vendors. We continuously innovate to provide products, solutions, and services that uphold the highest levels of security and certification.
Let's take a closer look at what you should consider when choosing an HSM vendor and what we guarantee when you choose Utimaco's General Purpose HSMs.
1. Superior Performance at Choice
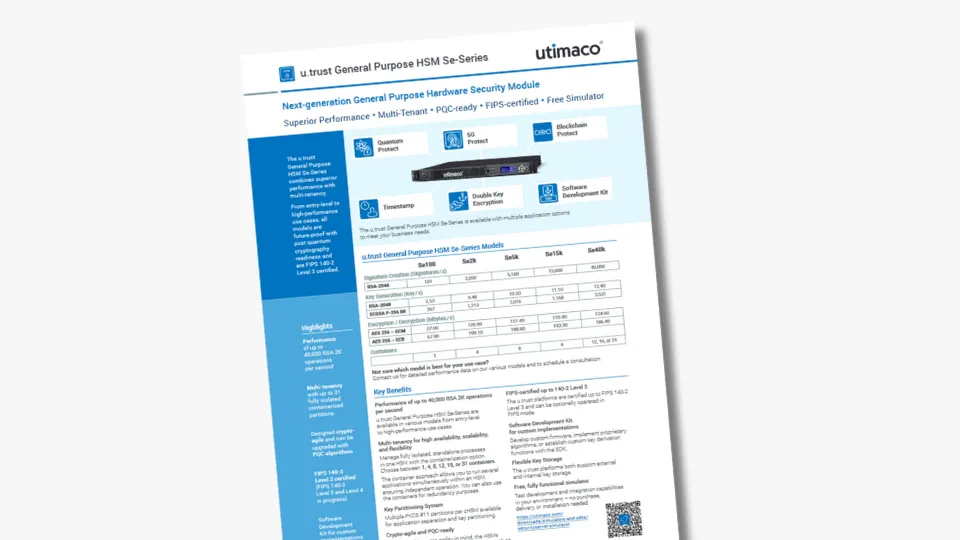
Performance is paramount in high-stakes environments, and Utimaco's HSMs deliver unrivaled speed and efficiency. From entry-level models to high-performance solutions capable of handling up to 40,000 RSA 2K signatures per second, Utimaco caters to a diverse range of requirements. Rigorous testing and optimization ensure that customers can rely on Utimaco's HSMs to meet even the most demanding workloads.
2. Multi-tenancy for High Availability and Scalability
With our platform's unique cloud-inspired architecture and multi-tenancy approach, we can provide unparalleled flexibility. We enable customers to tailor their HSM deployment to their specific needs, whether they opt for a single-purpose unit or use several containers for different, stand-alone applications.
This scalability ensures that organizations can adapt to evolving demands without compromising on performance or security. Each of the containers (cHSM) acts as a standalone HSM. Depending on the customer use case, Utimaco’s GP HSM portfolio offers performance option packs for:
- “Low-to-Medium performance use case” with 1 – 4 – 8 cHSMs,
- “Medium-High performance use case” with 4-12 cHSMs,
- For customer looking for multi tenancy on a big scale – e.g. CSP’s or big enterprise consolidating their internal IT infrastructure – we have options with 16 and 31 cHSMs,
- Independent of the number of containers in your HSM, each HSM provides multiple P11 slots per cHSM, allowing application separation and key partitioning.
3. PQC – Leading with Confidence in Theory and Practice
As the landscape of cryptographic standards evolves, Utimaco remains at the forefront, offering support for Post-Quantum Cryptography (PQC) algorithms recommended by NIST and BSI: CRYSTALS-Kyber, CRYSTALS-Dilithium, LMS, HSS, XMSS, and XMSS-MT.
We also have a market unique implementation for state handling of stateful hash-based signatures, which is already greatly appreciated by our customers. Through active participation in various PQC committees and working groups by NIST, the PKI Consortium, or ETSI, we play an important role in the standardization and implementation discussions.

4. Versatile Certification for Various Scenarios
In the world of Utimaco's GP HSMs, security isn't just a promise – it's certified to the highest standards.
All our GP HSMs are FIPS 140-2 Level 3 certified – running on u.trust General Purpose HSM Se-Series or CryptoServer platforms. For highest we also offer specialized HSMs that provide physical security according to FIPS 140-2 Level 4. Moreover, they are tailored to meet various compliance requirements, including eIDAS, VS-NfD, EU-restricted, NATO-restricted, and GSMA standards.
This versatility ensures that Utimaco's solutions can seamlessly integrate into diverse environments with stringent regulatory demands.
5. Flexibility by Design
Recognizing the importance of customization, Utimaco empowers customers with flexible solutions tailored to their unique requirements. With a comprehensive Software Development Kit (SDK) and support for proprietary algorithms, customers can customize their HSMs to suit specific use cases, e.g. by adding proprietary algorithms.
Flexibility is already important to us during the development process: that's why our HSMs are designed crypto agile – meaning they can be updated in field with new algorithms or updated standards. This is especially important for the transition phase from classical to post-quantum cryptography.
6. Free, Fully Functional Simulator
To facilitate seamless integration, we offer a free, fully functional simulator that is ideal for product evaluation. This tool allows customers to test the capabilities of Utimaco's HSMs without any financial commitment — it employs identical protocols and interfaces while providing support for all functionalities of the physical device.
By simulating real-world scenarios, customers can gain confidence in Utimaco's solutions and make informed decisions before proceeding with deployment. After testing, an easy transitioning to the deployment of the live HSM is possible.
Verify functionality of our simulator yourself, don't just take our word for it.
7. Transparent Licensing Made Easy
Complex pricing structures and hidden costs can often cloud the decision-making process. Utimaco simplifies this with a crystal-clear licensing model. Say goodbye to hidden costs and unexpected fees – with us, what you see is what you get.
Our straightforward approach means all standard algorithms are included, and there are no extra charges for partitions, ECC activation, remote management, or client licenses.
Here's what you can expect:
- All standard algorithms are included.
- Pricing aligned by performance.
- Fixed number of partitions included, upgrades possible with no hidden costs.
- No fees for ECC activation.
- No fees for remote management.
- No fees for additional users.
- Internal and external keystore support.
- External keystore based on Databases.
8. Seamless Integration with a Wide Array of Applications
Compatibility is key in today's interconnected ecosystem. Our GP HSM portfolio supports all common cryptographic APIs, facilitating integration with many applications. Whether it's banking systems, e-commerce platforms, or IoT devices, Utimaco's HSMs offer plug-and-play convenience, simplifying deployment and streamlining operations.
9. Customer Care: Going the Extra Mile
Beyond cutting-edge technology, we prioritize customer satisfaction. Our team of industry experts is committed to delivering personalized support and guidance, ensuring that every customer receives the attention and assistance they deserve. With a dedicated 24/7 support system in place, Utimaco goes above and beyond to address any queries or concerns promptly.
10. Available as a Service with 24/7 Support
For organizations seeking a hassle-free solution, Utimaco offers its GP HSMs as a service. Hosted in secure, certified data centers and backed by round-the-clock support, this option allows customers to offload the burden of setup, implementation, and maintenance. With our experts managing the infrastructure, customers can focus on their core business objectives with peace of mind.
11. Global Reach and Cybersecurity Partner Network
Last but certainly not least, Utimaco is equipped to assist customers from every corner of the globe, ensuring accessibility and support regardless of geographical location. Our global presence and partner network ensure efficient service delivery and support for clients across diverse regions.
Explore contact details for our local offices here! Learn more about our u.nity Partner Program here!
Our General Purpose HSMs showcase superior performance and power. Boasting post-quantum readiness, FIPS and Common Criteria Certification. For cybersecurity that you can trust, Utimaco is the better choice on-premises and as a service.
About the Author
Lena Backes is an IT Marketing expert with more than 10 years of experience working in the B2B sector. In her professional career, she has gained extensive knowledge in various areas, including cybersecurity, network management, enterprise streaming, and software asset management. In her current role she is responsible for product positioning of Utimaco’s cybersecurity products and solutions, with a particular focus on data protection, blockchain technology, and post quantum cryptography.