The race about quantum supremacy is on: new quantum computers with a higher number of qubits and more processing power are being presented each year.
Equipped with superior processing power, quantum computers are posing a serious threat to today’s cyber security. How is that? They can perform algorithms which have been designed to crack common cryptographic encryption methods – especially asymmetric encryption methods. Therefore, the research on quantum computers has a fundamental impact on the cyber security market.
Prepare for post quantum now
Although analysts and computing experts expect quantum computers to be available no more than 10 years from now, it is important to start preparing today, so that your organization will not be at risk in the future. Luckily, there are certain algorithms which are considered “quantum-proof”. Planning the migration to these algorithms is especially necessary for use cases which use asymmetric cryptography.
Get the white paper on Post Quantum Cryptography
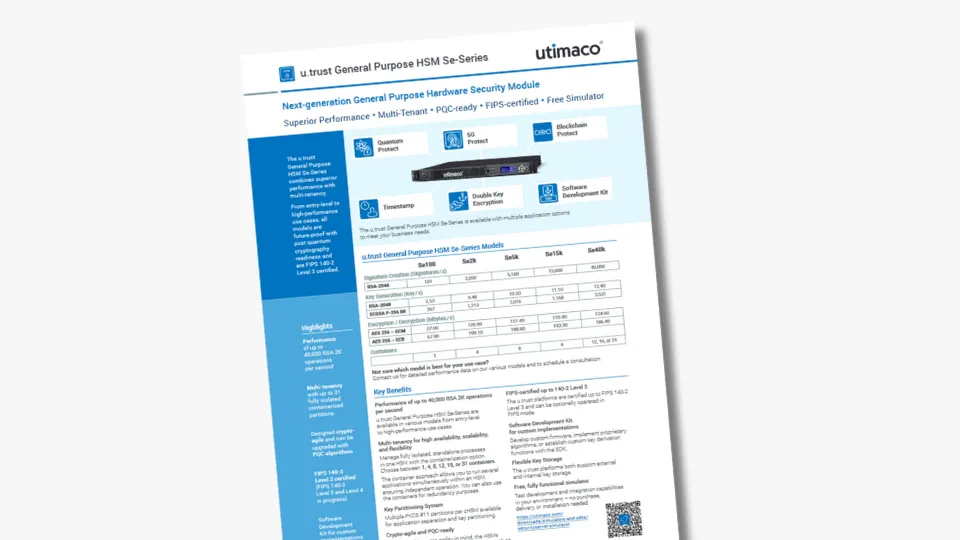
On the safe side: UTIMACO supports PQC algorithms recommended by NIST and BSI
UTIMACO is working on Post Quantum Cryptography for our products since several years. The result is an easy-to-integrate firmware extension, which includes quantum-proof algorithms recommended by NIST and BSI like: CRYSTALS-KYBER, CRYSTALS-Dilithium, HSS, XMSS, and XMSS-MT
Test your infrastructure’s readiness for PQC algorithms: Free Q-safe simulator