Definition: The most significant area of post-quantum cryptography is lattice-based cryptography. It is acclaimed for its efficiency and scalability, with use cases spanning from the fundamental cryptographic building blocks to immensely complex protocols.
Lattice-based Cryptography explained
There is an ongoing concern that a quantum computer will be able to crack existing cryptographic standards. Therefore, it became necessary to develop new standards for cryptography that would remain secure in the presence of quantum computers.
In contrast to current conventional methods, lattice-based cryptography (LBC) is one of the best-analyzed areas of post-quantum crypto. The name derives from the fact that this crypto scheme is built on mathematical problems around lattices. A lattice in this context resembles a grid of graph paper - using a set of points located at the crossings of a lattice of straight lines. This grid is not finite in any way. Instead, a lattice describes a pattern that continues into the infinite.
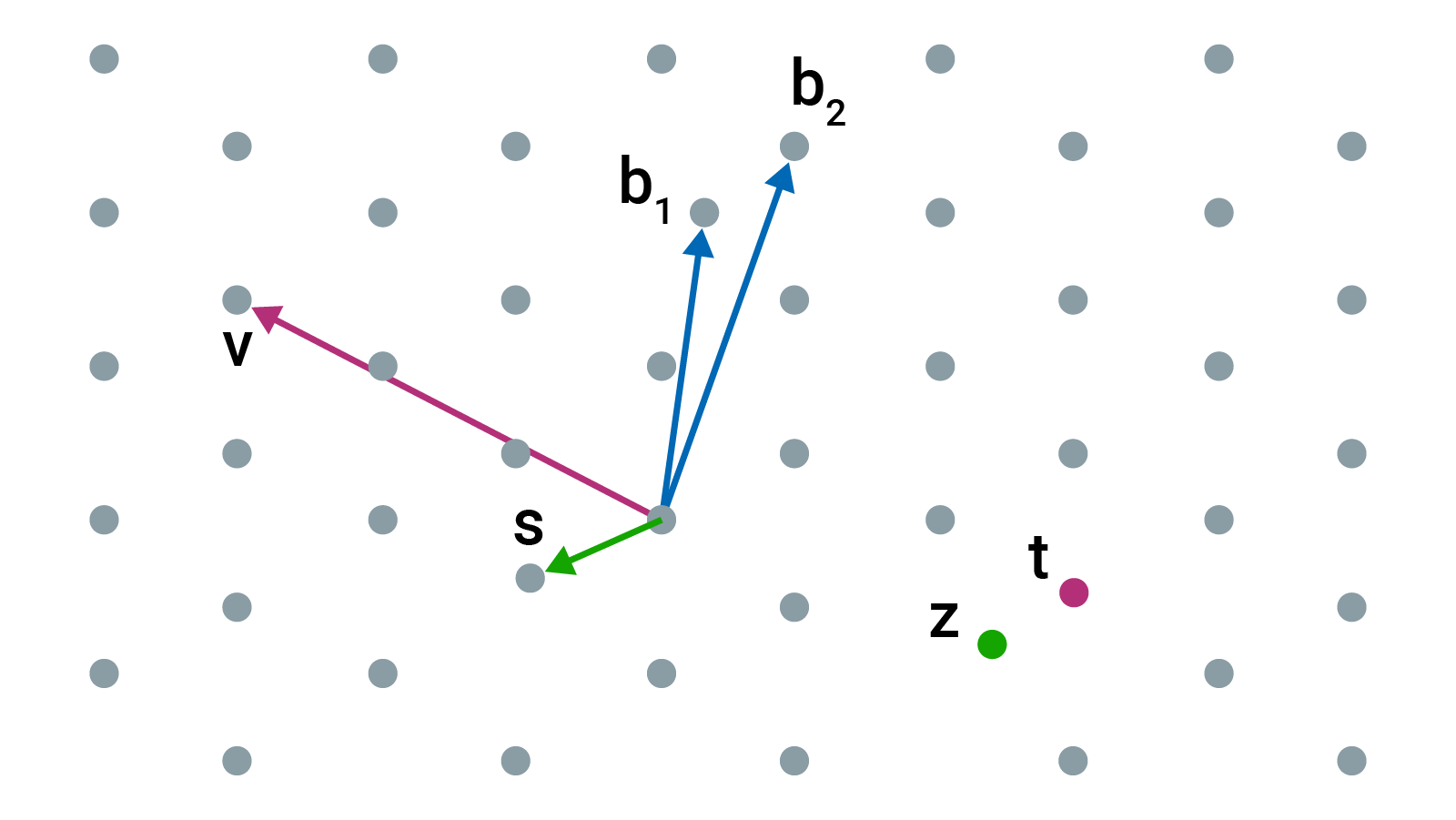
Starting with a set of points, known as vectors, numbers are then added and subtracted in any integer multiples. The hard problem is finding points in the lattice that are close to 0 or close to some other point. These problems are quite simple in 2 dimensions, but they become extremely challenging in 400 dimensions, for example. Within the diagram above, an example would be that one set of points could be the private key and another set of points that are further away could be the public key.
A brute force search of all possibilities would be necessary to deduce the private key from the public key, and even if quantum computers can speed up this search, it would still take a sizable and unrealistic amount of time. Even a quantum computer is thought to be unable to solve hard problems based on lattices in a reasonable period of time.
Lattice-based schemes are also the only contender left in the NIST process for providing the fundamental primitives of encryption, key encapsulation and digital signature schemes (DSSs). Examples of lattice-based algorithms are CRYSTALS-KYBER (a public key encryption and key-establishment algorithm) and CRYSTALS-Dilithium (a digital signature algorithm).
By providing standardized post-quantum cryptography (PQC) algorithms, researchers can create cryptographic systems that are secure against both quantum and conventional computers and can interoperate with existing communication protocols and networks.
Utimaco is able to provide quantum-resistant solutions that enable businesses to defend their systems against assaults based on quantum computers thanks to significant time and talent investments in post-quantum cryptography.








