Securing the most valuable Assets in the Automobile Life Cycle
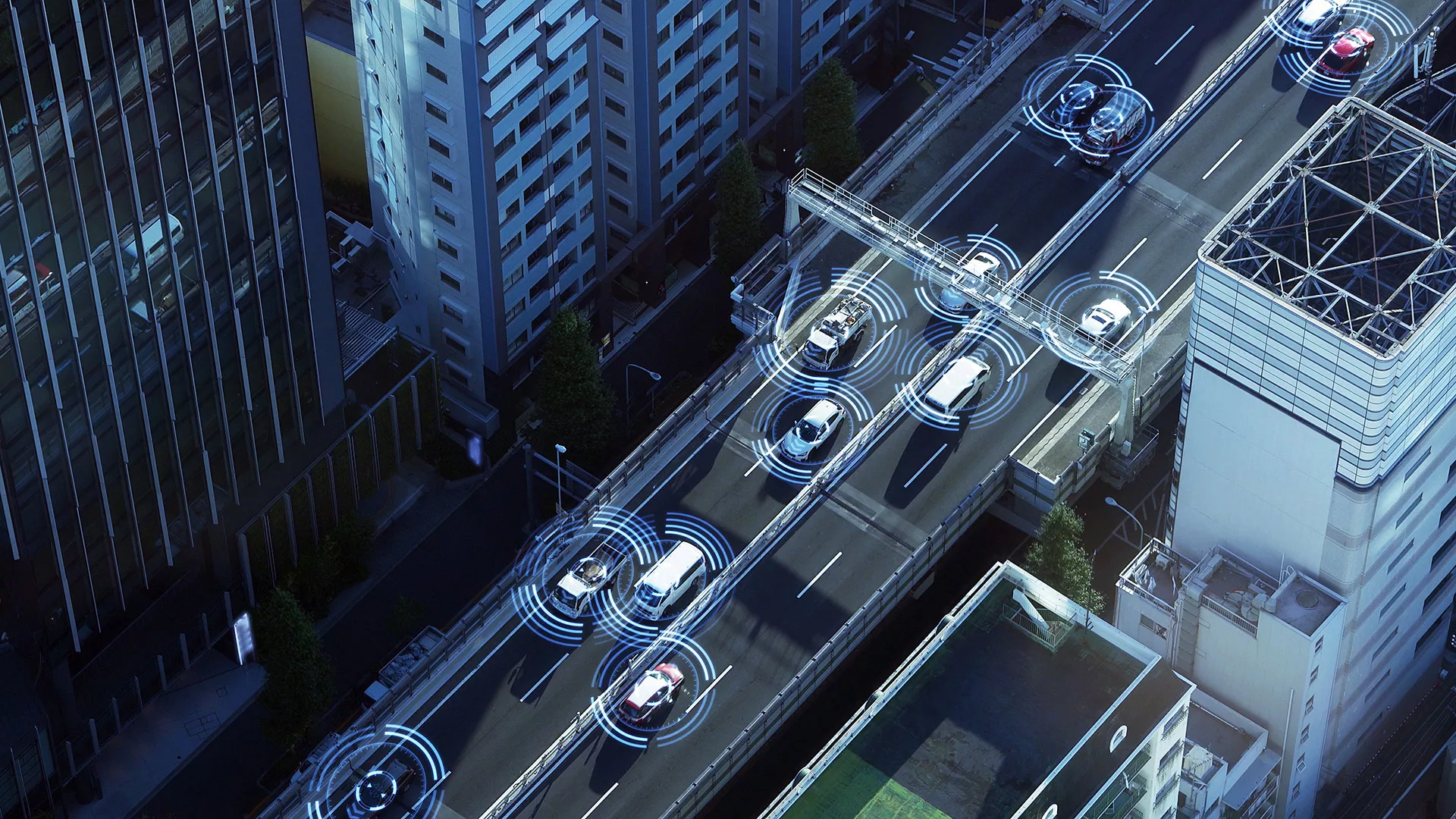
Cars are becoming more digitized, increasing the need for cybersecurity solutions to protect operational and personal data. As not just the car itself but also its parts, manufacturer and related service getting more and more connected, the number of vulnerabilities and potential security and threat vectors arise.
The connected car exchanges data in an increasing extend with other cars vehicles-to-vehicle communication (V2V) or with its infrastructure elements, e.g. with a mobile phone (vehicle-to-infrastructure (V2I).
Even the information exchange about hazards on the route ahead or transport information (vehicle-to-everything (V2X) is no longer a future scenario. The resulting number of touchpoints provides an equal number of possible data security gaps which can lead to data loss or the stealth and misuse of personal data. This also extends to third parties like insurance companies who need access to the data collected by the car. Securing, the digital components including unique identification for it’s full life cycle such as updates, recalls and sun setting is crucially important. The data anonymization to meet the regulations such as GDPR becomes increasingly important for the safety of the driver and passengers.