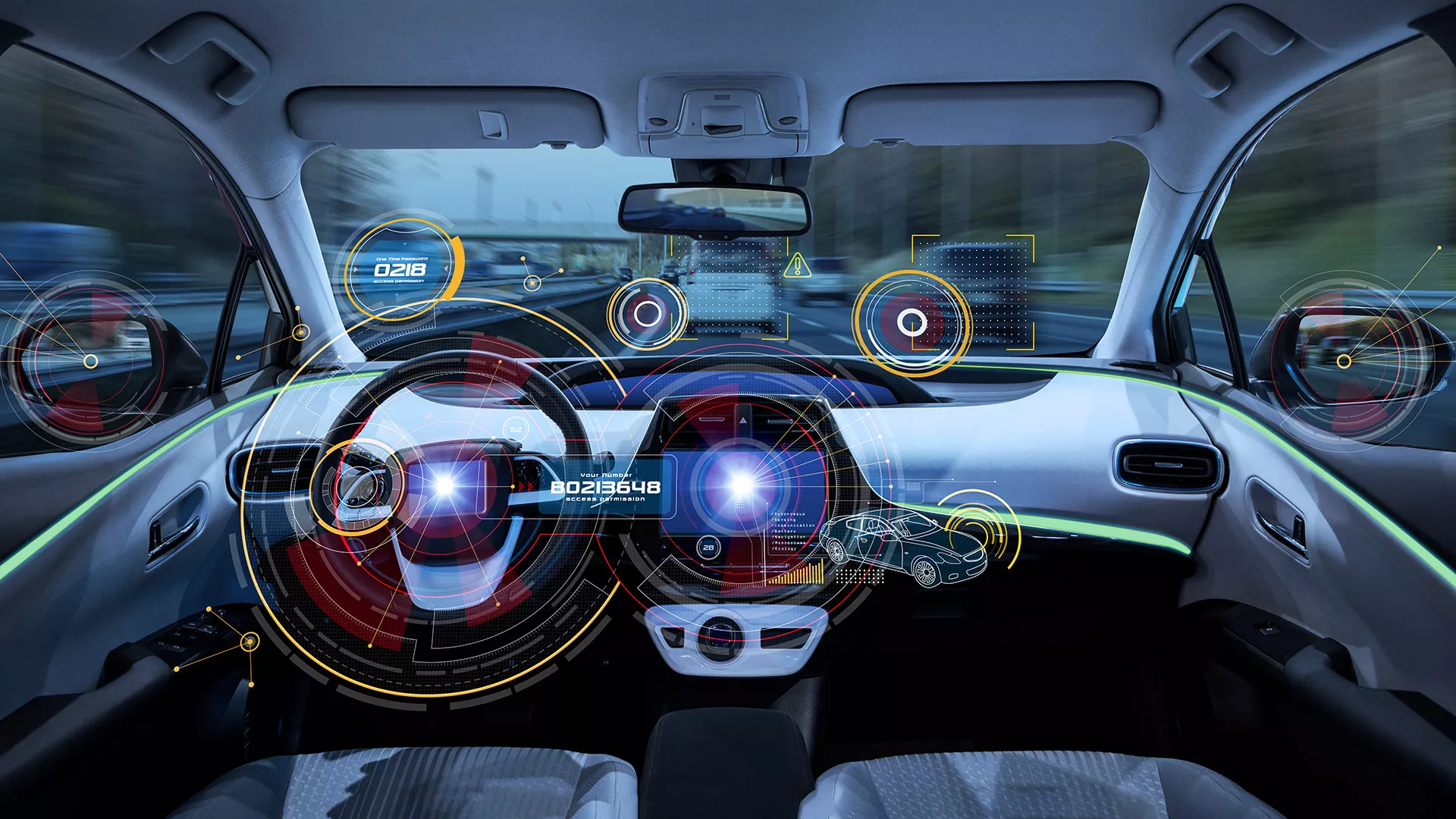
Securing the data on connectivity links (Ethernet) between Electronic Control Units (ECUs)
With car technology rapidly increasing, various advancements such as high-powered entertainment systems, navigation, interactive systems, driver response performance, are seen in the market. To support them, Ethernet is becoming an essential part of the Automotive E/E Architecture as a connectivity link that connects various ECUs for the aforementioned high-end applications.
With the need to protect the data transported on Ethernet, a data security protocol, like MACsec, is used. MACsec provides point-to-point security on Ethernet links. This enables the confidentiality of transmitted data in the network of ECUs, preventing disruption and data loss caused by unauthorized parties.